Payroll Pirates Target Workday and Others
Hackers
December 12, 2024
Analysts began monitoring a phishing scam known as “Payroll Pirates” that involves payroll redirection and primarily targets employees of various organizations, particularly those using Workday. The threat actors use malicious SEO poisoning and spoofed Human Resources (HR) pages to trick victims into providing employee portal credentials. Once they gain account access, they change banking information to redirect payroll funds to threat actor-controlled accounts.
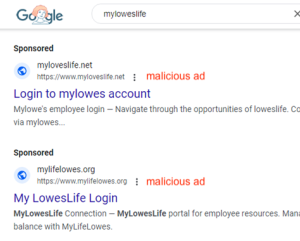
Several domains linked to various prominent organizations, such as the California Employment Development Department, Kaiser Permanente, Home Depot, Aldi’s, and Macy’s, have been identified. In August, analysts reported a similar campaign that targeted Lowe’s by imitating its HR portal structure. Website builders like Leadpages, Mobirise, and Wix are used to quickly establish domains in these campaigns. Phishing content is often hosted through registrars such as Dynadot, Porkbun, and Namecheap.
Analysts developed queries to monitor campaign activities and, within a few hours, identified over 100 new domains potentially linked to the campaign, highlighting the threat actor’s efforts to expand their network. Additionally, dedicated IP ranges were incorporated into the new infrastructure, reflecting strategic changes corresponding to specific timeframes. One notable IP address, 193.3.19[.]112, was linked to previous scams. Some domains initially featured the HTML title “MyPay” before changing to “hrkp.”
Recommendations
- In the event of a successful payroll diversion, contact your HR department immediately upon detection.
- Avoid clicking links and opening attachments in unsolicited emails.
- Confirm requests from senders via contact information obtained from verified and official sources.
- Type official website URLs into browsers manually.
- Facilitate user awareness training to include these types of phishing-based techniques.
- Ensure MFA is enabled for all online accounts.
- Consider leveraging behavior-based detection tools rather than signature-based tools.
- Ingest indicators of future attacks found in the Silent Push blog post into endpoint security solutions and consider leveraging behavior-based detection tools rather than signature-based tools.