Phishing Campaign Uses Adobe Acrobat
Scams
June 13, 2024
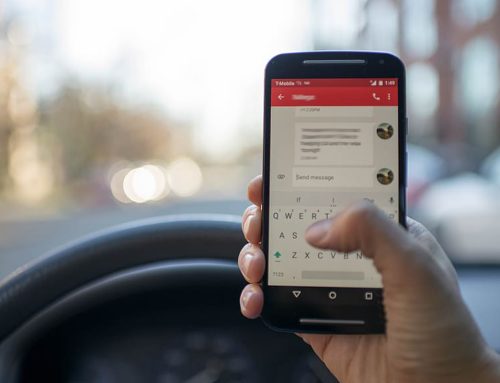
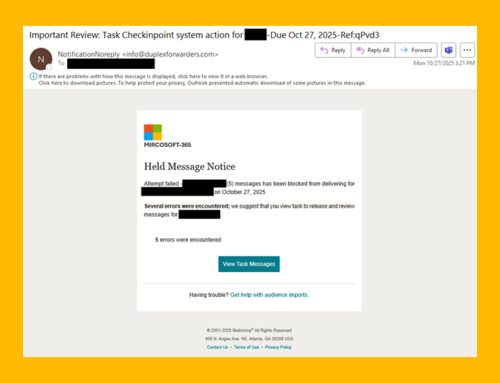
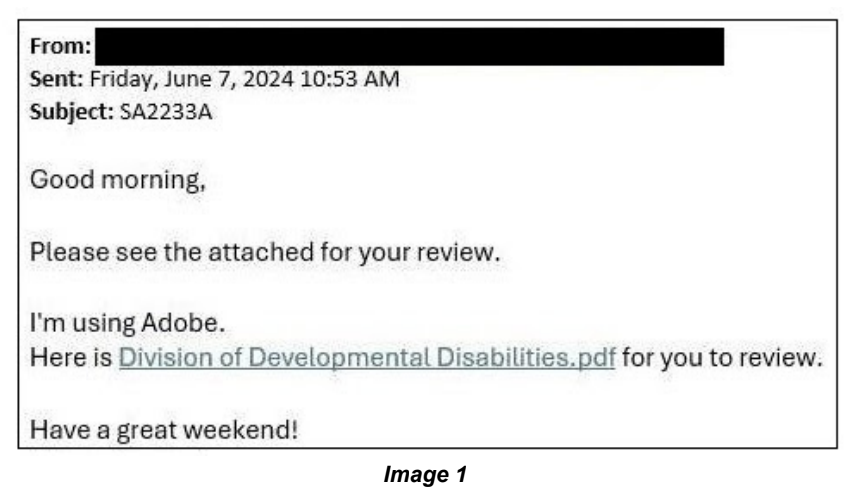
The NJCCIC recently observed an uptick in phishing campaigns targeting New Jersey State employees using a legitimate file-sharing platform and URL redirects to steal user credentials and deliver malware. In one scheme, an email (image 1) includes an embedded Adobe Acrobat link to view an invoice in an attempt to harvest credentials (image 2).
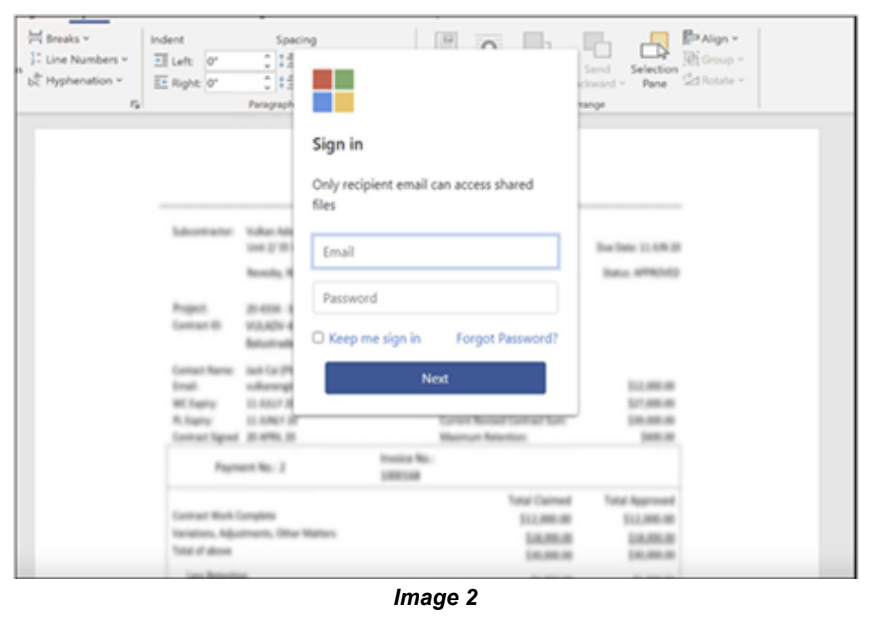
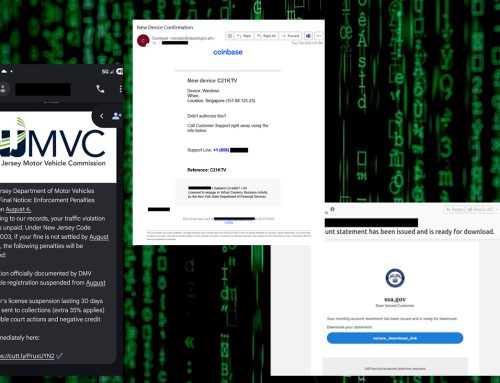
If the user clicks the “next” radio button, a dialogue box pops up asking if the user would like to open the link (image 3) “hxxps[://]mysexdollscanada.ca/p/ ?cmFuZDE9Uk[…].”

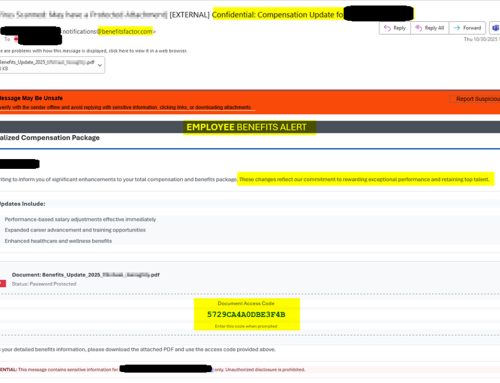
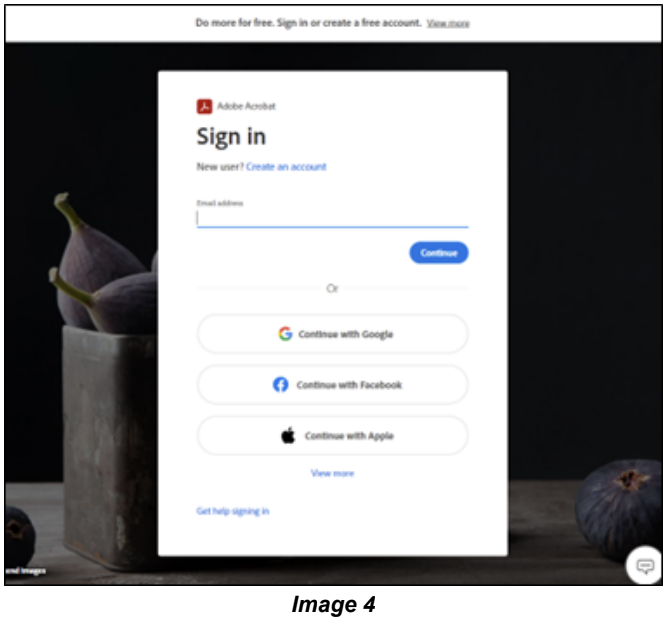
Another Adobe link (image 4) used to steal credentials in this campaign is “hxxps[://]acrobat[.]adobe[.]com/id/urn:aaid:sc:US:bb41cf5e-284e-4a6c-9449-a7843ab3e343.”
The cyber threat actors behind the campaign collect user account credentials submitted on the fraudulent webpage to facilitate subsequent cyber threat activity. Acquiring account credentials may be more successful when the recipients perceive that the communication originated from a familiar and trustworthy source. Additionally, using a legitimate service such as Adobe lends credibility to the scheme. While most of the emails associated with this campaign were quarantined by the email security solution for suspicious behavior, some emails successfully bypassed condemnation by using a compromised known user email for delivery.
Recommendations
- Avoid clicking links, responding to, or otherwise acting on unsolicited text messages or emails.
- Implement email filtering solutions, such as spam filters, to help block messages. The New Jersey Email Authorization & Authentication Set Up PDF and the Sender Policy Framework – SPF Guide NJCCIC products provide information on establishing DMARC authentication.
- Keep systems up to date and apply patches after appropriate testing.
- Install endpoint security solutions to help protect against malware.
- Use strong, unique passwords and enable multi-factor authentication (MFA), choosing authentication apps or hardware tokens over SMS text-based codes.
- Reduce your digital footprint to reduce the likelihood of becoming a target for malicious actors.
- Participate in security awareness training to help better understand cyber threats, provide a strong line of defense, and identify red flags in potentially malicious communications.
- Further recommendations to avoid victimization can be found in the NJCCIC products Credential Harvesting and Compromise and Don’t Take the Bait! Phishing and Other Social Engineering Attacks.