Phishing for Bank Credentials
Scams
October 31, 2024
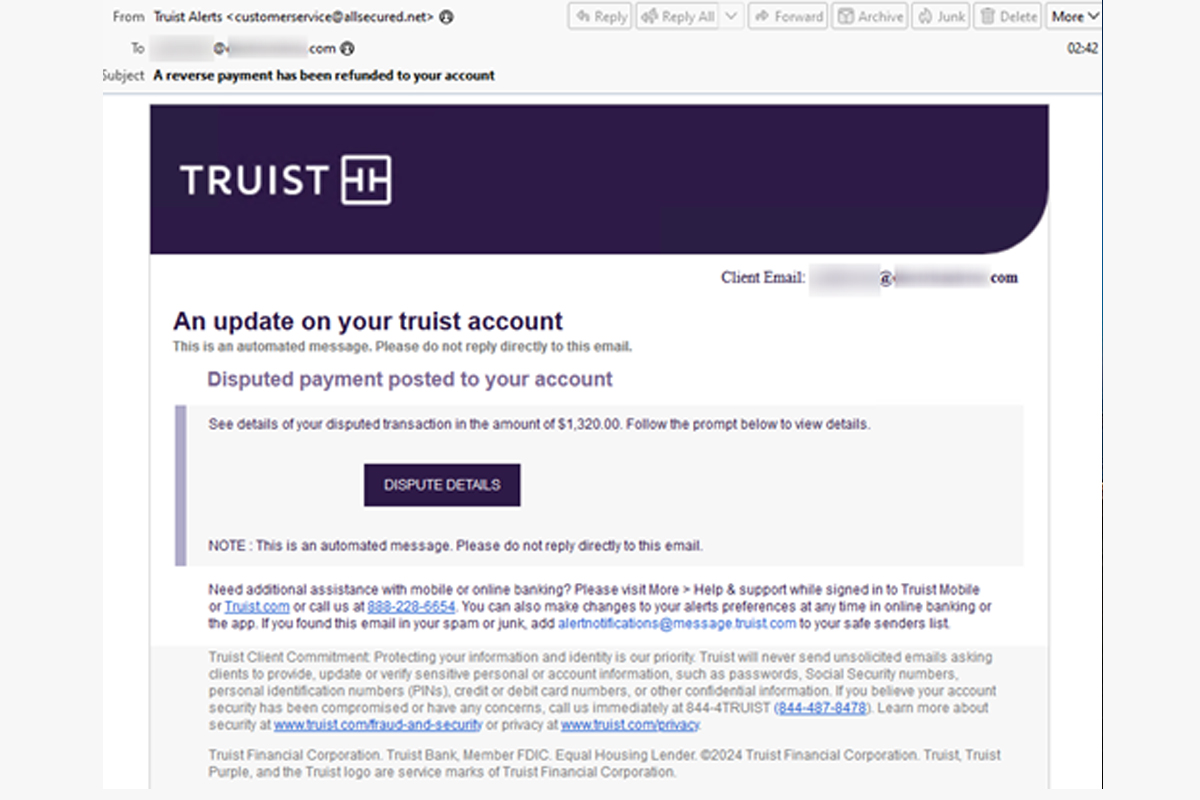
The NJCCIC’s email security solution has observed an uptick in phishing attacks impersonating Truist Bank and Wells Fargo Bank. These emails were flagged for using uncommon URL domains, abused URL services, and uncommon senders. While the emails appear well-crafted and legitimate at first glance, there are still a few signs to look out for:
- Unusual Sender: Emails appear to originate from an email address typically used by the bank.
- Suspicious Link: The link may initially appear legitimate; however, threat actors often use deceptive URLs to redirect targets to a malicious website.
- Rush Tactics: Threat actors create a sense of urgency, such as stating that there is a payment dispute, to cause potential victims to act without verifying the legitimacy.
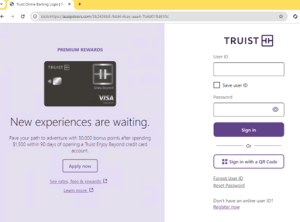
Once a link is clicked, users are redirected to a well-crafted login page that harvests user banking credentials and, if submitted, forwards them to the threat actors. In some scams, the domain may be a typosquatted version of the legitimate website; however, in this campaign, the threat actors left the URL clear and recognizable, relying on users to sign in without verifying.
Recommendations
- void clicking links and opening attachments in unsolicited emails.
- Confirm requests from senders via contact information obtained from verified and official sources.
- Type official website URLs into browsers manually.
- Facilitate user awareness training to include these types of phishing-based techniques.
- Maintain robust and up-to-date endpoint detection tools on every endpoint.
- Consider leveraging behavior-based detection tools rather than signature-based tools.
- Report suspicious activity to the FBI’s IC3 and NJCCIC.