Phishing for (Stolen) Information
Malware
August 1, 2024
The NJCCIC observed an uptick in campaigns aiming to spread Formbook infostealing malware. Formbook is classified as malware-as-a-service (MaaS), though it was originally advertised as browser-logger software. Formbook can extract data from HTML forms and gain access to keystrokes, browsers auto-fill information, and clipboard data.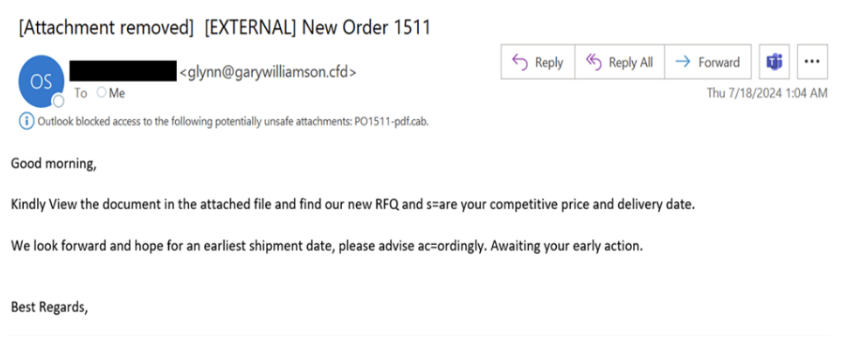
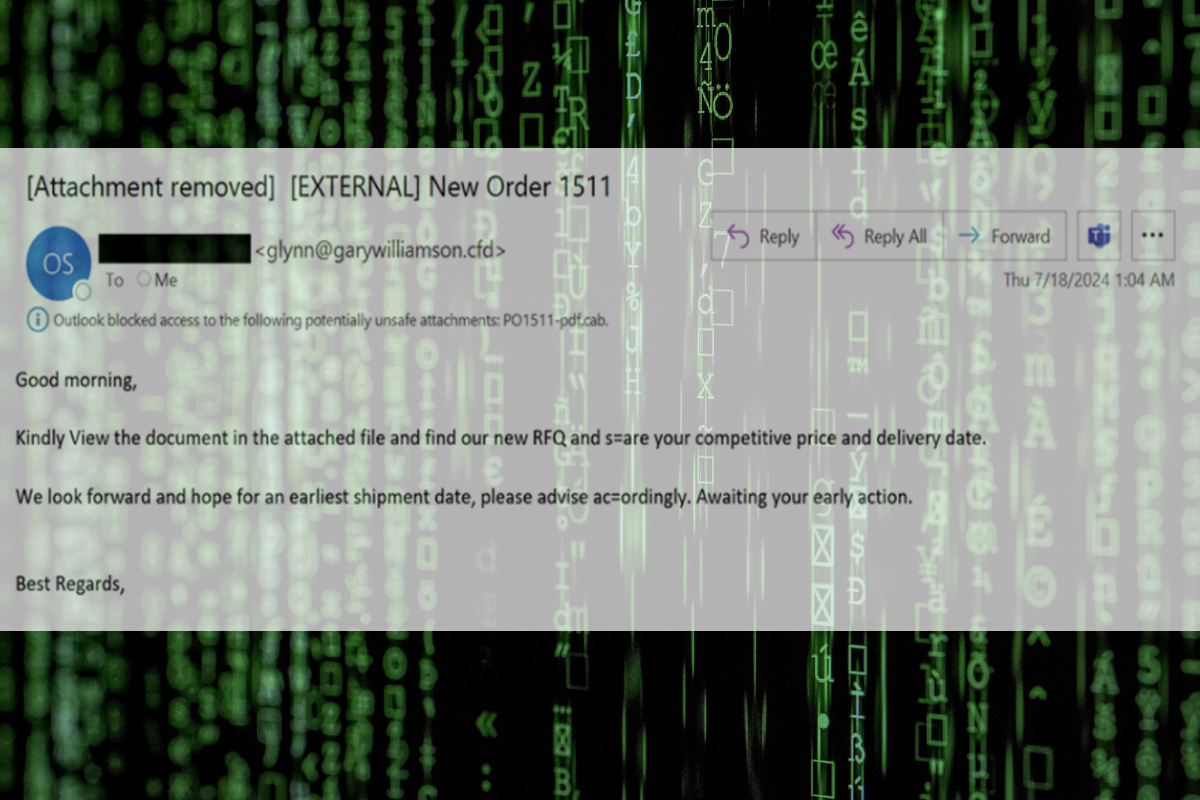
The email campaign spotted by Proofpoint included messages claiming to be Requests for Quotations (RFQ), purchasing orders, or invoices. The emails contained compressed executables that utilized Packager Shell Objects (OLE) to exploit vulnerabilities found in Equation Editor. After successful exploitation, LCG Kit downloads and installs Formbook, XLoader, Agent Tesla, and LokiBot. This is a new variation of a recurring campaign by the cyber threat group TA2536.
In May, security researchers discovered phishing attacks targeting small and medium-sized businesses (SMB) in Poland, Italy, and Romania. This campaign spread several malware types, including Formbook, Agent Tesla, and Remcos RAT. Threat actors imitated existing businesses and their employees to add legitimacy to their emails.
Recommendations
- Avoid clicking links and opening attachments in unsolicited emails.
- Confirm requests from senders via contact information obtained from verified and official sources.
- Type official website URLs into browsers manually.
- Facilitate user awareness training to include these types of phishing-based techniques.
- Maintain robust and up-to-date endpoint detection tools on every endpoint.
- Consider leveraging behavior-based detection tools rather than signature-based tools.