Phishing Kits Used to Bypass MFA
Scams
March 28, 2024
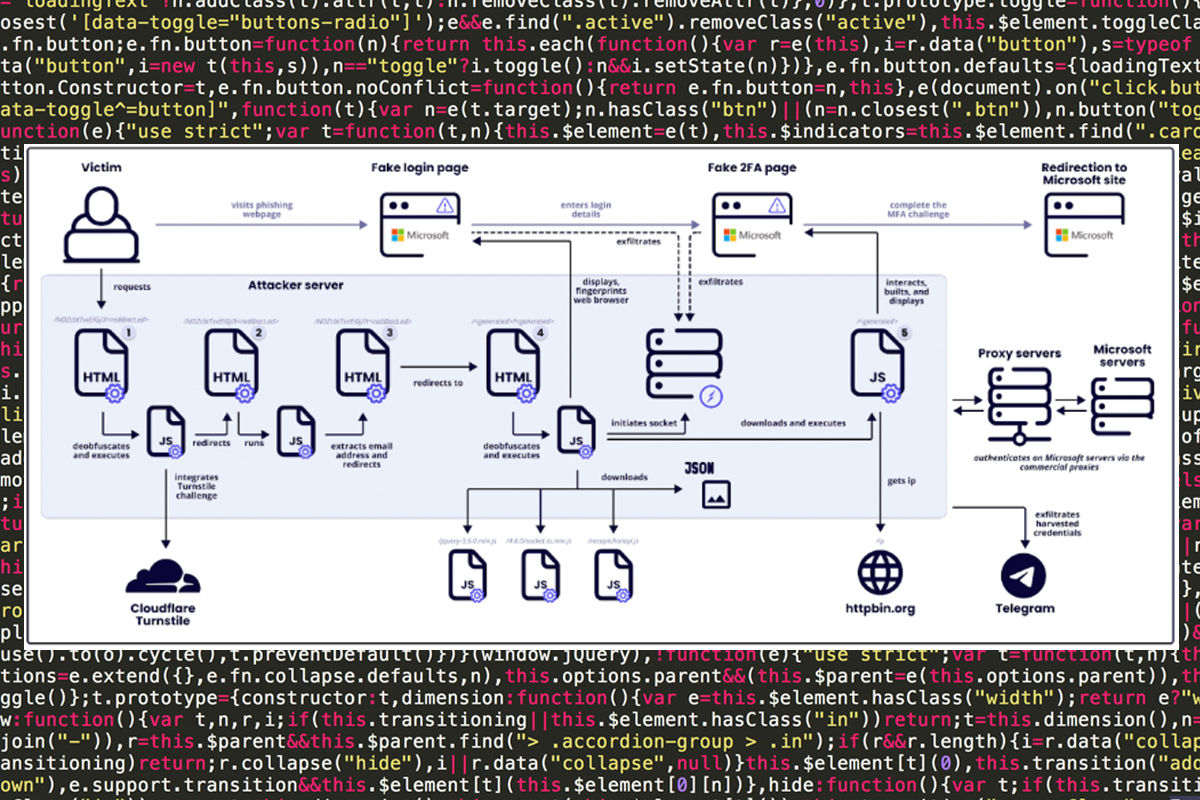
As more users adopt multi-factor authentication (MFA) to bolster their account security, threat actors increase efforts to bypass this security measure. Threat actors often use phishing emails to gather login details for online accounts and, in some cases, use phishing kits (also known as phishing-as-a-service platforms) to increase the effectiveness of these campaigns. One kit, “Tycoon 2FA,” targets Microsoft 365 and Gmail accounts and can bypass the services’ 2FA/MFA. A recent version released in 2024 leverages more domains and improves the program’s capabilities to block analytic tools and filter traffic. While Tycoon 2FA has been active since August 2023, the use of the kit increased around October 2023 and has been observed in thousands of phishing attacks. Tycoon bypasses MFA by stealing session cookies and replaying the user’s session on a legitimate service, such as Microsoft 365 or Gmail. Additional details on Tycoon 2FA and each stage of the attack can be found in the Sekoia blog post.
The NJCCIC advises users to enable MFA on all online accounts and choose more secure methods, such as authentication apps or hardware tokens, over less secure methods, such as SMS- or email-based codes. Users should only log into their accounts on official websites, refraining from clicking links in unverified emails or text messages. If you suspect your account has been compromised, reset your password, log out of all devices, and delete any unauthorized rules set up on the account. Network defenders may utilize the indicators of compromise related to Tycoon 2FA found in the Sekoia blog post.