Phishing With Corrupted Files
Scams
December 5, 2024
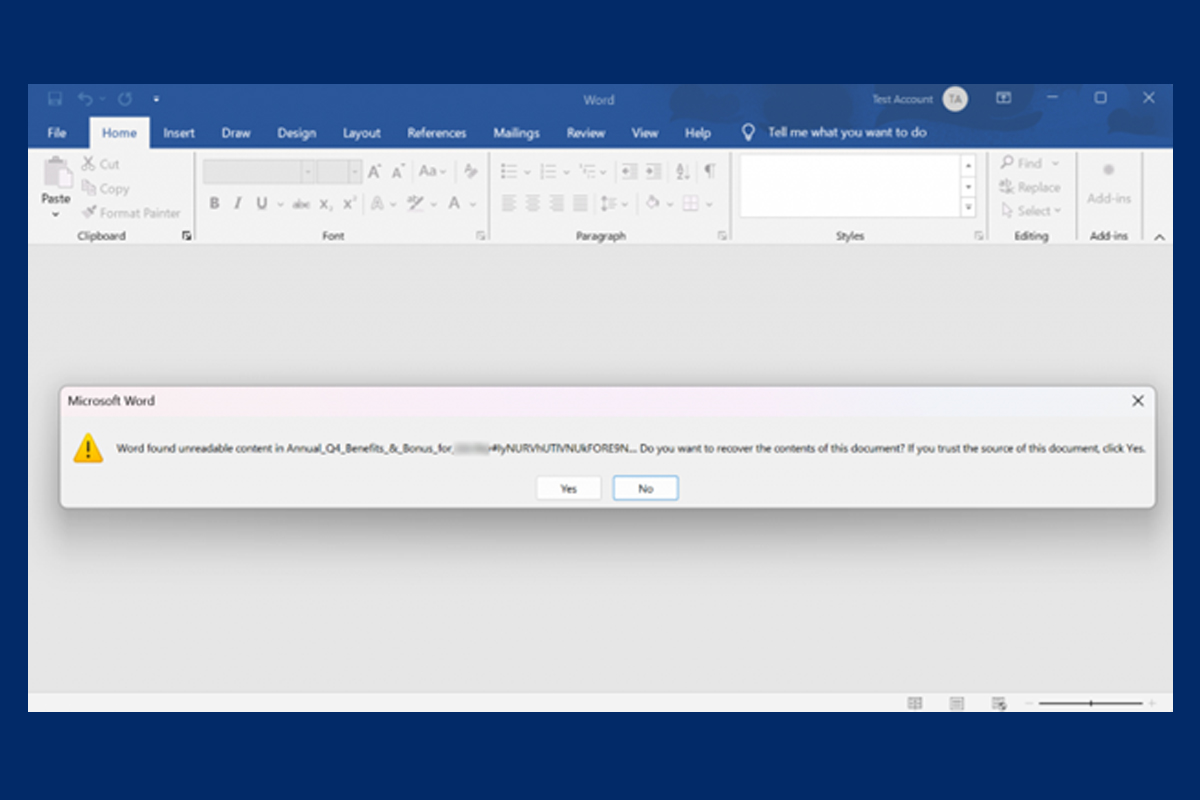
Researchers have discovered a new phishing campaign utilizing Microsoft’s Word file recovery feature. In this campaign, threat actors exploit the corrupted file state to disguise the file type and evade detection by security tools. These emails pretend to be sent from human resources and payroll departments and include attachments that claim to be bonuses, benefits, and payments. The attachments include the same base64 encoded string “IyNURVhUTlVNUkFORE9NNDUjIw,” which decodes to “##TEXTNUMRANDOM45##.” An error message displays upon opening the corrupted file, stating that Microsoft Word found unreadable content and provides the option to recover the file if the sender is trusted.
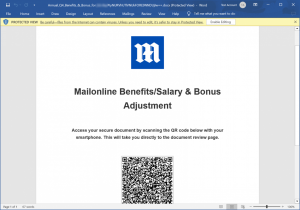
The recovered Microsoft Word document includes a logo from the targeted company and a malicious quick-response (QR) code claiming to direct the target to the document needing review. Upon scanning the QR code, targets are redirected to a site that poses as a Microsoft login page. Any entered credentials are forwarded to threat actors.
Recommendations
- Avoid clicking links and opening attachments in unsolicited emails.
- Confirm requests from senders via contact information obtained from verified and official sources.
- Type official website URLs into browsers manually.
- Facilitate user awareness training to include these types of phishing-based techniques.
- Maintain robust and up-to-date endpoint detection tools on every endpoint.
- Consider leveraging behavior-based detection tools rather than signature-based tools.
- Report malicious activity to the FBI’s IC3 and NJCCIC.