PowerSchool Student Information Breach
Individual Attacks
January 9, 2025
The NJCCIC was notified that a recent data breach impacted several school districts that use PowerSchool’s student information system (SIS) platform. PowerSchool is a cloud-based third-party software provider for K-12 schools, serving over 60 million students globally. The software allows K-12 districts to manage various operations via convenient platforms, such as enrollment, communication, attendance, staff management, learning systems, analytics, and finance. In addition, they operate Naviance, a platform that many K-12 districts use to provide students with personalized tools for college, career, and life readiness planning.
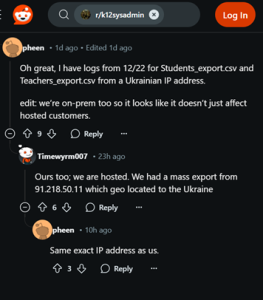
The breach was discovered on December 28, 2024, when unauthorized access to customer information was detected on their PowerSource customer support platform. Some impacted districts reported unauthorized activity as early as December 22 associated with the IP address, 91[.]218[.]50[.]11, geolocated to Ukraine. Some also noted that the maintenance user was identified as “200A0” in the ps-log-audit files. This maintenance user is linked to the PowerSource “export data manager” customer support tool that the threat actor used to exfiltrate data.
The threat actor used compromised credentials to access the PowerSource maintenance access tool, which allows IT professionals to access customer SIS instances for support and troubleshooting. The threat actor then exported the sensitive data via a CSV file. While the stolen information primarily includes names and addresses, it may also contain Social Security numbers, personally identifiable information, medical information, and grades for some districts.
PowerSchool clarified that the incident was not a traditional ransomware attack; however, they did pay a ransom to prevent the release of data. Although they were shown a video that allegedly confirmed the deletion of all copies of the data, there is no guarantee that this was fully effective. As a precaution, PowerSchool is monitoring the dark web for any potential leaks.
IT personnel whose school districts were impacted shared further insights to detect indicators of compromise. The investigation is ongoing, and a finalized report is expected to be distributed by January 17, 2025. Additional information can be found in the BleepingComputer article. Malicious cyber activity can be reported to the FBI’s IC3 and the NJCCIC.