PowerShell Scripts in Phishing Campaigns
Scams
June 20, 2024
The NJCCIC’s email security solution observed two new phishing campaigns utilizing PowerShell scripts to drop multiple malicious payloads. One campaign, dubbed ClickFix, launched by a threat actor identified as TA571, which was also behind the recently observed DarkGate phishing campaign. ClickFix shares many similarities to a second campaign known as ClearFake, and analysts spotted a significant overlap of tactics, techniques, and procedures (TTPs) between the two campaigns.
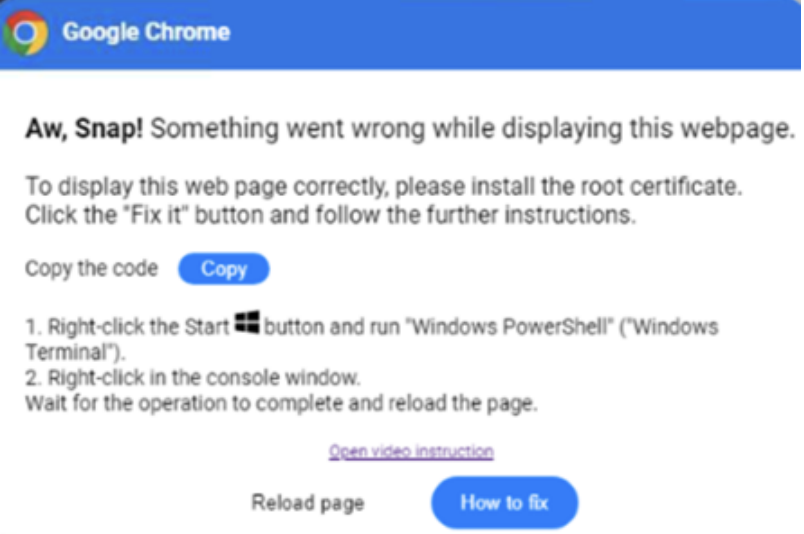
ClearFake uses a technique called EtherHiding, which uses the blockchain of Binance’s Smart Chain contracts to host a malicious script. This script is injected into compromised websites and loads a second script once a user visits. The secondary script triggers a fake overlay warning to appear, claiming that a root certificate needs to be installed for the website to appear correctly, and includes instructions on how to copy and execute a PowerShell script as a purported solution. If the PowerShell script is executed, the following actions will take place:
- Flushes the DNS cache.
- Clears clipboard content to remove traces of the malicious script.
- Runs a second PowerShell script that downloads Lumma Stealer.
- Lumma Stealer downloads three additional payloads.
- Amadey Loader
- XMRig cryptocurrency miner
- Clipboard Hijacker
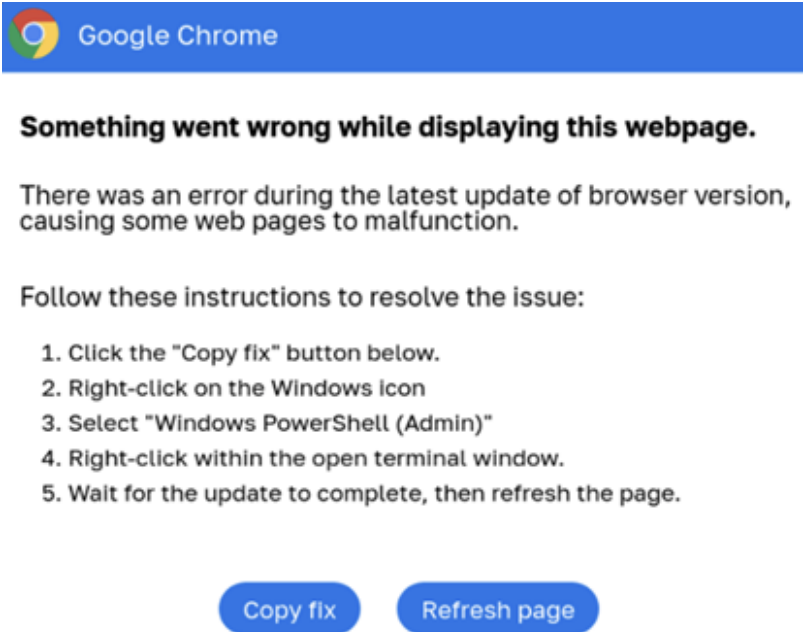
Like ClearFake, the ClickFix campaign begins with an overlay warning on a compromised website stating that a recent browser update was faulty and offers a PowerShell script as a fix. ClickFix was initially observed leading to an infection from a Vidar Stealer payload but has since changed its infection chain, leading to the same payloads as the ClearFake campaign. Researchers are still determining if the threat actors behind the two campaigns work together or if ClearFake replaced the code of the already compromised ClickFix iframes.
Recommendations
- Avoid clicking links and opening attachments in unsolicited emails.
- Confirm requests from senders via contact information obtained from verified and official sources.
- Type official website URLs into browsers manually.
- Facilitate user awareness training to include these types of phishing-based techniques.
- Maintain robust and up-to-date endpoint detection tools on every endpoint.
- Consider leveraging behavior-based detection tools rather than signature-based tools.
- Phishing and other malicious cyber activity can be reported to the FBI’s IC3 and the NJCCIC.
For any further questions, contact us here at Cyber Command.





