Ransomware Threats Gaining Momentum
Ransomware
December 12, 2024
Ransomware continues to dominate the threat landscape, posing significant risks to organizations. The NJCCIC continues to receive reports of ransomware incidents impacting New Jersey private and public sector organizations, including educational institutions and local governments. Fog ransomware and 3AM ransomware are two significant variants that have emerged in the past year. They continue to gain momentum and will likely remain among the top threats in 2025.
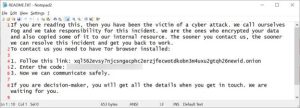
Fog ransomware, a variant of the STOP/DJVU family, emerged in early May 2024 and primarily targets Windows and Linux endpoints in education, recreation, travel, and manufacturing in the United States. By early fall, there was an uptick in Fog ransomware incidents that included these and other high-value industries. It leverages compromised VPN credentials to gain access to victim environments. The PsExec tool is deployed to several hosts, and RDP/SMB protocols are used to access targeted systems. Threat actors sometimes employ “pass the hash” attacks on administrator accounts to establish RDP connections to Windows servers running Hyper-V and Veeam. They also use credential stuffing to move laterally and hijack valuable accounts. Fog disables security defenses, encrypts Virtual Machine Disk (VMDK) files in virtual machine (VM) storage, quietly deletes backups from Veeam, and removes Windows volume shadow copies to prevent recovery. Encrypted files are also appended with a .fog or .flocked extension, and a ransom note is displayed on affected systems. Threat actors utilize double extortion tactics to leverage stolen data and demand hefty ransoms.
- Refrain from clicking links, responding to, or acting on unsolicited emails.
- Navigate directly to legitimate websites and verify before submitting account credentials or providing personal or financial information.
- Use strong, unique passwords for all accounts and enable multi-factor authentication (MFA) where available, choosing authentication apps or hardware tokens over SMS text-based codes.
- Keep systems up to date and apply patches after appropriate testing.
- Maintain robust and up-to-date endpoint detection tools on every endpoint.
- Consider leveraging behavior-based detection tools rather than signature-based tools.
- Utilize network segmentation to isolate valuable assets and help prevent the spread of ransomware and malware.
- Enforce the principle of least privilege, disable unused ports and services, and use web application firewalls (WAFs).
- Establish a comprehensive data backup plan that includes regularly performing scheduled backups, keeping an updated copy offline in a separate and secure location, and testing it regularly.
- Report ransomware and other malicious cyber activity to the FBI’s IC3 and the NJCCIC.





