Rockstar 2FA and PhaaS Kits
Scams
December 5, 2024
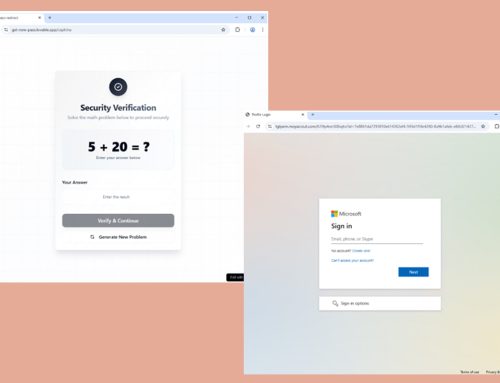
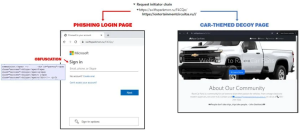
Commodity phishing attacks, known as Phishing-as-a-Service (PhaaS) kits, remain prevalent due to their low cost, anonymity, and ease of execution. Advanced in-the-middle (AiTM) techniques allow attackers to bypass additional security measures such as MFA. Cybercriminals use fraudulent apps and websites to steal victims’ personal and financial information, often resulting in significant financial losses, with some individuals reporting losses exceeding $10,000. Consequently, the likelihood of secondary attacks increases, including account takeovers, phishing campaigns using compromised accounts, or business email compromise (BEC).
- Document and file-sharing notifications
- E-signature platform-themed messages
- HR and payroll-related messages
- MFA lures
- IT department notifications
- Password/account-related alerts
- Voicemail notifications
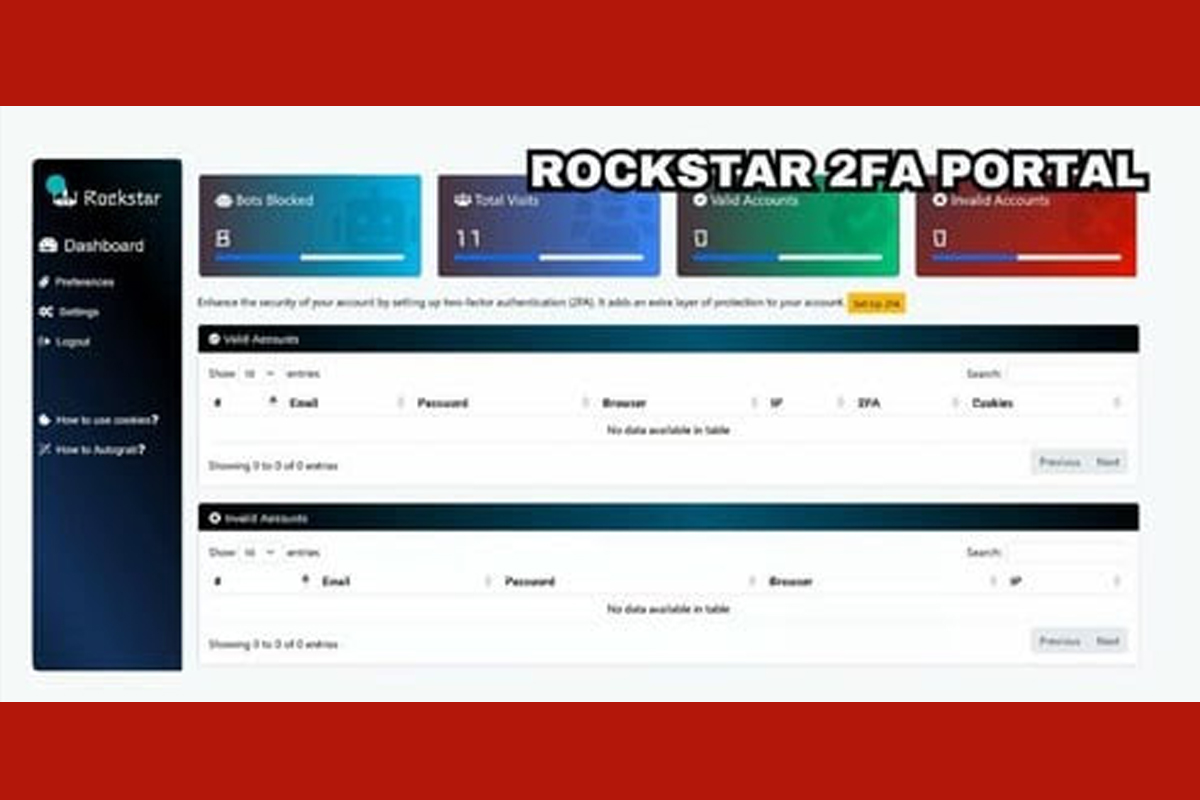
Marketing posts from Telegram promote Rockstar 2FA’s various features, including anti-bot protection, multiple login page themes, randomized source codes and attachments, Telegram bot integration, and a user-friendly admin panel. Rockstar 2FA is offered for as little as $200 for a two-week subscription service and provides options for monthly subscriptions and one-time payment alternatives.
Since May 2024, urlscan.io has recorded over 3,700 hits related to a campaign using the URL format “hxxps?:\/\/{URLDOMAIN}\/{
Recommendations
- Educate yourself and others about these and similar scams.
- Refrain from clicking on links and attachments delivered via emails or social media messages.
- Avoid clicking links or acting on unsolicited text messages or emails and refrain from divulging sensitive information or providing funds.
- Implement cybersecurity best practices to reduce risk and increase resiliency to cyber threats.
- Keep systems up to date and apply patches after appropriate testing.
- Use strong, unique passwords and enable MFA for all accounts where available, choosing authentication apps or hardware tokens over SMS text-based codes.
- Use email filters and consider monitoring Telegram and other dark web activity to track PhaaS TTPs.
- Ingest IOCs found in the Trustwave blog posts (1, 2, 3 ) into endpoint security solutions and consider leveraging behavior-based detection tools rather than signature-based tools.