Cyber Security Back to Basics
Security
April 3, 2025
When it comes to securing networks, data, and accounts, cybersecurity professionals often focus on advanced security controls and tools that can help identify and prevent malicious and suspicious activity. While this is valid, we may fail to spotlight the necessity for fundamental IT security practices before we can address more complex cybersecurity controls and implementations.
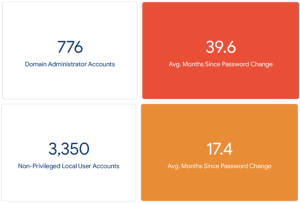
Based on a sample of NJ organizations, the NJCCIC found many organizations do not adequately follow industry standards for password management or, more broadly, identity and access management. On average, local, non-privileged user account passwords were last changed nearly 1.5 years ago, while domain administrator account passwords were last changed well over three years ago. Given the rate at which passwords are compromised through data breaches, malware, and methods such as credential stuffing, changing passwords infrequently poses a significant risk to these networks. If passwords are obtained, the accounts are left open to access particularly when a secondary method of authentication is not required, as with multi-factor authentication (MFA). If accounts are compromised, threat actors can use this access to obtain a foothold in the associated network and facilitate subsequent malicious activity.
A lack of restrictions on user permissions increases the risk associated with account compromises, as regardless of the user account, the threat actors will gain considerable network access. Identifying this access could be difficult as the threat actor uses a legitimate account to carry out their activity. By employing the Principle of Least Privilege , however, the damage associated with a compromised account is better contained, the network’s attack surface is minimized, and the risk of accidental or malicious misuse is reduced. This principle can be applied to users, administrators, and systems for improved cybersecurity.
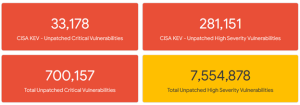
In addition, the organizations sampled fail to apply patch management practices that adequately mitigate vulnerabilities, leaving critical vulnerabilities unpatched. Among the approximately 200 organizations sampled, over 33,000 critical vulnerabilities left unpatched are identified in CISA’s Known Exploited Vulnerabilities (KEV) catalog as actively exploited by cyber threat actors. Furthermore, many devices on these networks are end-of-life, such as Windows Server 2008 and 2012 and Windows 7, which means updates are no longer available and the devices are left vulnerable.

|
A way to address these fundamental IT security issues is by using identity and access management (IAM) tools, such as Active Directory with Group Policy (GP) or Entra ID , in conjunction with its cloud-based management services like Intune and configuration manager. These tools significantly assist administrators in establishing fundamental cybersecurity controls to better secure networks. Administrators can manage and secure users and systems by configuring settings, behaviors, and privileges. Administrators may set password complexity requirements, password expiration, account lockout policies after failed login attempts, and user authentication requirements, such as MFA. MFA is an essential security control for account security, and these tools assist administrators in ensuring compliance. Additionally, administrators can define acceptable software that can be used on the network, block unapproved software or file types, and define trusted software and paths. Using these tools, administrators can control user and device permissions to limit access to sensitive data, prevent unauthorized system configuration changes, and restrict access to network resources. They can also enable auditing and logging for specific actions on the network, allowing administrators to identify suspicious activity and provide network visibility. Administrators can also enforce file and device encryption to protect data from unauthorized access if a device is lost or stolen. Furthermore, administrators may use group policy or configuration management tools to enforce update settings across the environment, ensuring that all systems are regularly patched and up to date, further reducing the network’s attack surface.
While there are many other cybersecurity controls that can and should be implemented, addressing these issues is fundamental to an organization’s cybersecurity program and will significantly reduce their cyber risk.
|





