SocGholish Targets Vulnerable Websites
Malware
March 2, 2023
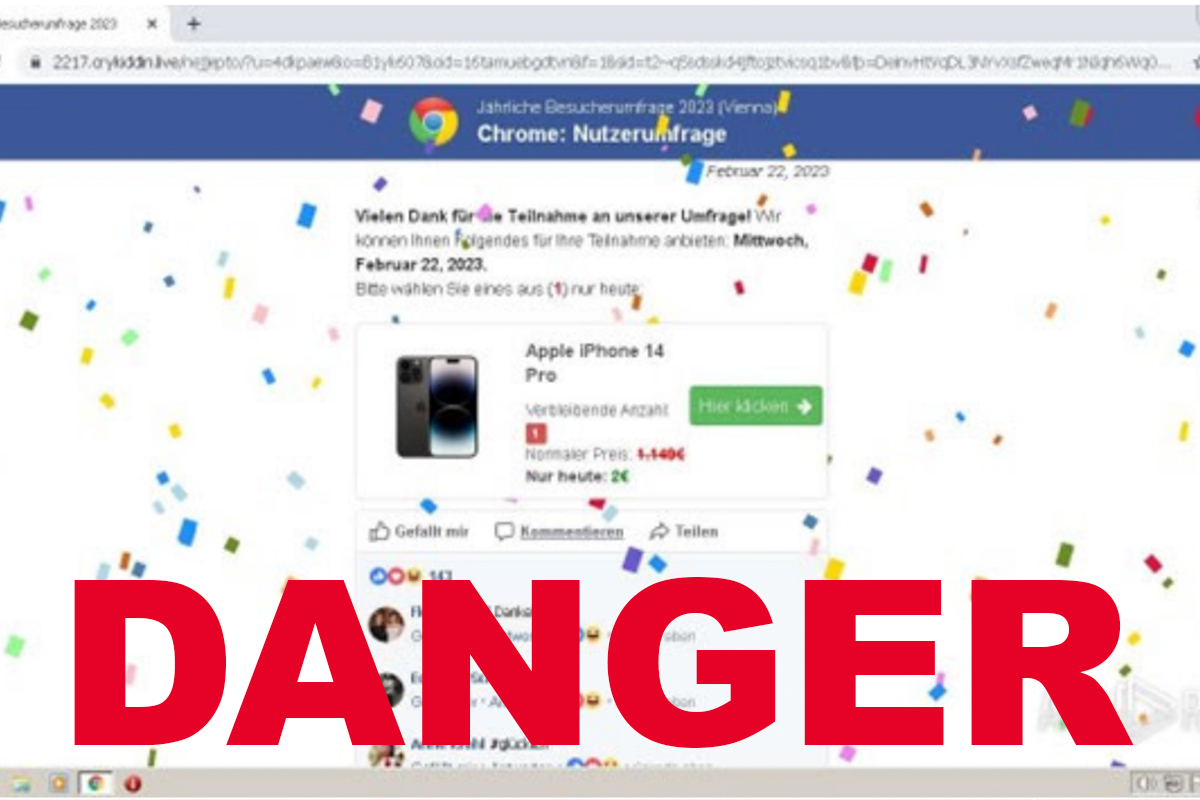
Over the last several months, the NJCCIC observed websites containing malicious artifacts indicative of a SocGholish infection. SocGholish is a malware loader that exploits vulnerable website infrastructure and can perform reconnaissance and deploy malicious payloads, such as remote access trojans (RATs), information stealers, and ransomware. In one recently observed campaign, the compromised website immediately redirected the user through several links, finally landing on a webpage that claimed the user won a free iPhone. The user is prompted to enter personal information such as their name, home address, and email address to receive the gift. Additionally, many of the redirected links, such as greatbonushere[.]life and crykiddin[.]live, were flagged as malicious. The compromised website is believed to have been initially infected due to one or more vulnerable plugins. Throughout 2022, SocGholish infections significantly increased, targeting vulnerable websites that led to subsequent infections and network compromises.
The NJCCIC advises website administrators to keep websites, associated applications, and plugins up to date, uninstall unused or deprecated components and plugins, and actively monitor for unauthorized changes. Additionally, establish strong passwords and use multi-factor authentication (MFA) where available, employ the Principle of Least Privilege to reduce the impact of a potential incident, and keep backups of the website available and offline. Recent tactics, techniques, and procedures (TTPs) and indicators of compromise (IOCs) can be found in the Proofpoint Threat Insight post and SentinelOne report.
For any further questions, contact us here at Cyber Command.