Social Engineering Targeting Healthcare
Scams
June 25, 2024
The Federal Bureau of Investigation (FBI) and the Department of Health and Human Services (HHS) released this Joint Cybersecurity Advisory to disseminate known indicators of compromise (IOCs) and tactics, techniques, and procedures (TTPs) used in a social engineering campaign targeting healthcare, public health entities, and providers. Threat actors are using phishing schemes to steal login credentials for initial access and the diversion of automated clearinghouse (ACH) payments to US controlled bank accounts. Healthcare organizations are attractive targets for threat actors due to their size, technological dependence, access to personal health information, and unique impacts from patient care disruptions. While based on incidents in the Healthcare and Public Health (HPH) sector, all sectors are encouraged to review the advisory to reduce the likelihood and impact of social engineering incidents.
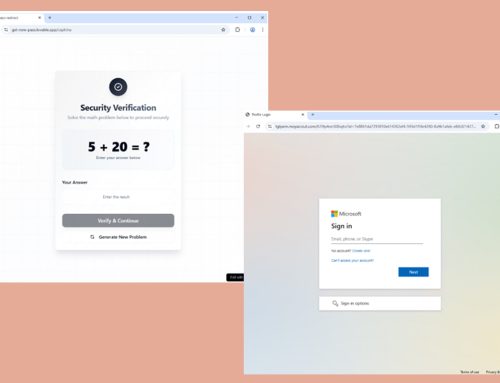
Based on previous cyberattacks and forensic analysis reports, the FBI and HHS observed consistency in TTPs used in cyberattacks against the HPH sector. Unknown threat actors gained initial access to employees’ email accounts and then pivoted to specifically target login information related to the processing of reimbursement payments to insurance companies, Medicare, or similar entities. Threat actors acquired credentials through social engineering or phishing to gain initial access to victim networks. In some observed instances, threat actors called an organization’s IT Help Desk posing as an employee of the organization, and triggered a password reset for the targeted employee’s organizational account. In some instances, by manipulating the IT Help Desk employees, threat actors were able to bypass multi-factor authentication (MFA). In another instance, threat actors registered a phishing domain that varied by one character from the target organization’s true domain and targeted the organization’s Chief Financial Officer. Threat actors often have personally identifiable information (PII) of the impersonated employee, obtained from data breaches, enabling them to confirm the targeted employees’ identity over the phone. If a social engineering attempt is successful, the threat actors then logged into the victim account and attempted to use living off the land techniques (LOTL). LOTL gives threat actors the ability to conduct their malicious cyberattacks discreetly as they can camouflage activity with typ Save ical system and network behavior. By using LOTL, threat actors were able to amend forms to make ACH changes to patients’ accounts, which enabled the diversion of legitimate payments to US bank accounts controlled by the threat actors, followed by a second transfer of funds to overseas accounts. In some instances, threat actors also attempted to upload malware to victim systems without success.
The FBI and HHS encourage organizations to implement the recommendations in the mitigations section of this advisory to reduce the likelihood and impact of social engineering incidents.
For any further questions, contact us here at Cyber Command.