Threat Actors Evade Detection
Security
October 17, 2024
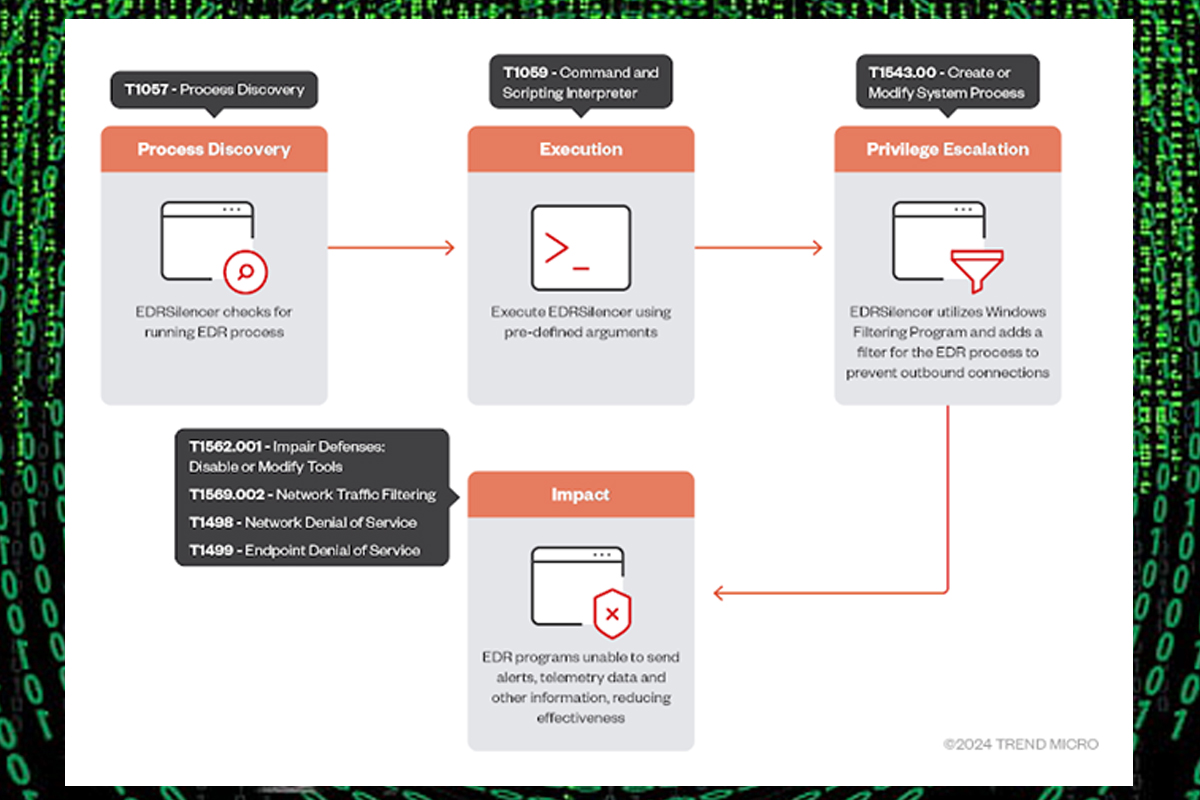
Ransomware groups frequently use Endpoint Detection and Response (EDR) tools like AuKill, EDRKillShifter, and others to disable security systems. Threat actors were recently observed incorporating the open-source tool EDRSilencer into their attack strategies to disrupt EDR solutions and conceal malicious activities. EDRSilencer can stop processes associated with various EDR products from companies such as Microsoft, Palo Alto Networks, and Fortinet, making malware detection and removal difficult.
EDRSilencer is similar to the closed-source tool NightHawk FireBlock, which blocks outbound traffic when EDR processes are active using the Windows Filtering Platform (WFP). WFP allows developers to create custom rules for filtering network traffic based on criteria such as IP addresses and ports, helping protect systems. EDRSilencer scans for active EDR processes and uses WFP filters to prevent them from sending alerts. Threat actors will continue to develop advanced tools to circumvent security measures, which may allow malware to remain undetected.
Recommendations
- Implement a defense-in-depth strategy using multiple layers of security controls, including firewalls, intrusion detection systems, anti-virus software, and EDR. Creating redundancy can reduce risk and increase resiliency to cyber threats.
- Keep systems up to date and apply patches after appropriate testing.
- Enforce the principles of least privilege, use strong, unique passwords, and enable multi-factor authentication (MFA) for all accounts where available, choosing authentication apps or hardware tokens over SMS text-based codes.
- Ensure operational technology (OT) environments are segmented from information technology (IT) environments.
- Perform scheduled backups regularly, keeping an updated copy offline in a separate and secure location and testing it regularly.
- Conduct continuous monitoring and threat hunting. Ingest indicators of compromise (IOCs) and techniques found in the Trend Micro report into endpoint security solutions and consider leveraging behavior-based detection tools rather than signature-based tools.