Threat Actors Hijack Sitting Ducks
Hackers
November 21, 2024
Threat actors continue to employ the “Sitting Ducks” technique to hijack legitimate domains for phishing and investment fraud. Analysts reported nearly 800,000 vulnerable domains in three months, with about 9 percent subsequently hijacked. This method exploits misconfigurations in Domain Name System (DNS) settings, allowing attackers to claim domains without access to the owner’s account.
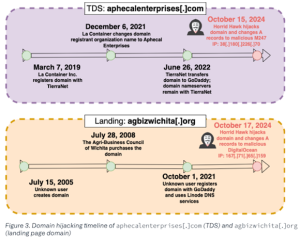
Detection of these hijacks is challenging due to the reputable status of the affected domains, which include well-known brands and non-profits. Additionally, rotational hijacking occurs when different threat actors repeatedly take control of the same domain, often leveraging free DNS services for short-term use. These hijacked domains facilitate various malicious activities, including malware distribution and credential theft, while remaining largely undetected by security vendors.
Prominent threat actors using the Sitting Ducks technique include:
- acant Viper: used to operate the 404 TDS, malicious spam operations, deliver porn, establish command-and-control (C2), and drop malware such as DarkGate and AsyncRAT.
- Horrid Hawk: used to conduct investment fraud schemes by distributing the hijacked domains via Facebook ads.
- Hasty Hawk: used to conduct widespread phishing campaigns that primarily mimic DHL shipping pages and fake donation sites.
Recommendations
- These attacks can be prevented by ensuring the correct configurations are in place for the domain registrar and DNS providers.
- WordPress website administrators are encouraged to carefully inspect website and event logs for signs of infection.
- Regularly monitor and check for backdoor code, and the addition or alteration of any admin accounts.
- Keep all website themes, plugins, and other software up to date, remove unused plugins and themes, and utilize a WAF.
- Inspect, clean, and protect all websites hosted under the same server account. Isolate important websites with separate server accounts to prevent malware propagation from adjacent websites.
- Use strong, unique passwords for all accounts and enable MFA where available, choosing authentication apps or hardware tokens over SMS text-based codes.





