Impersonating Financial Institutions
Malware,Scams
June 29, 2023
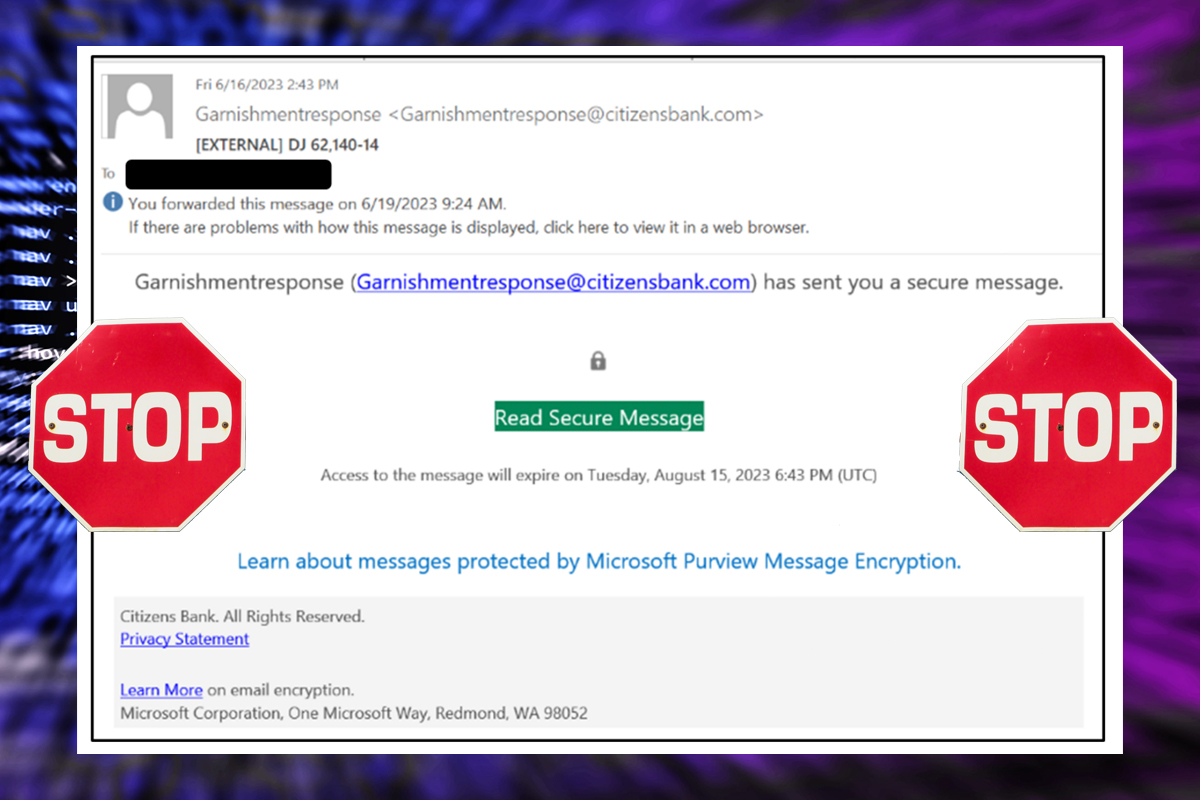
The NJCCIC received reports of targeted, well-crafted phishing emails claiming to be from financial institutions, specifically Citizens Bank. In the above example, the sender’s display name impersonates Citizens Bank to convey legitimacy. Additionally, the phishing email contains an embedded link that, if clicked, initiates the malware infection chain historically associated with various executables . The email headers revealed that the signature did not match the domain name, and the IP address was unauthorized to send from the domain used, resulting in a failed DMARC authentication. The threat actor used language to incite concern regarding possible garnished wages.
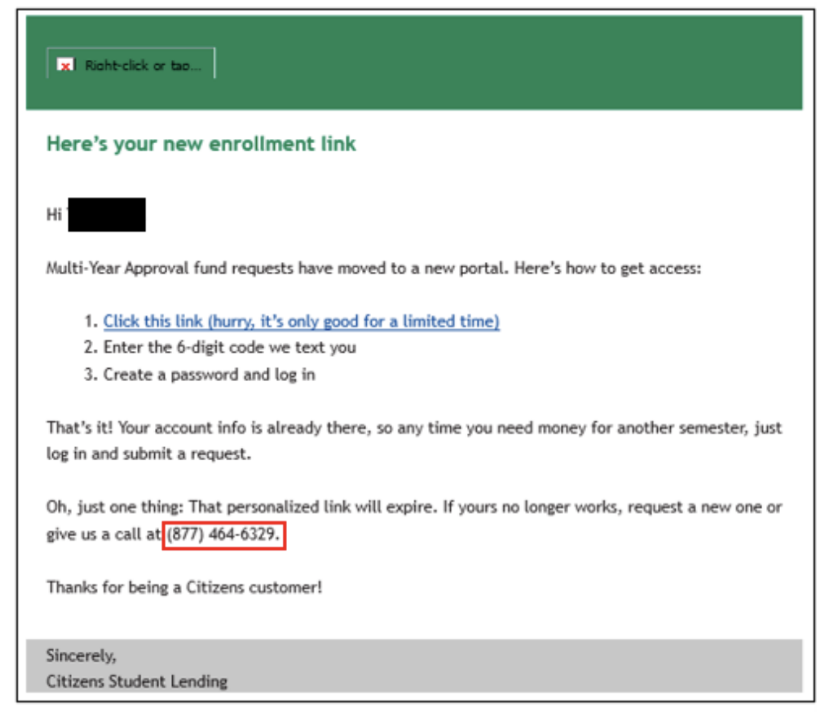
Another example included indicators of attack (IOAs) that were almost identical to those in the first example; however, this phishing email targeted a Citizens Bank student loan customer. The threat actor again used verbiage to instill a sense of urgency and concern, as the target did not receive a text from Citizens Bank. The target attempted to verify the included phone number and found that it did not match the financial institution’s student lending department. In this example, the embedded link directed the user to a login page that attempts to steal the user’s credentials if entered.
The NJCCIC recommends users refrain from responding to unsolicited communications, opening attachments, or clicking links from unknown senders, and exercise caution with communications from known senders. If unsure of the legitimacy, contact the sender via a separate means of communication, such as by phone, before taking any action. Phishing emails and other malicious cyber activity can be reported to IC3 and the NJCCIC. Further guidance to establish DMARC authentication can be found in the NJCCIC products, New Jersey Email Authorization & Authentication Set Up PDF and the Sender Policy Framework – SPF Guide.