Threat Actors Hand in Microsoft’s Cookie Jar
Hackers
June 26, 2025
The NJCCIC’s email security solution observed a phishing campaign aimed at harvesting Microsoft account credentials, multi-factor authentication (MFA) tokens, and associated session cookies. Messages in this campaign appear to come from DocuSign, Edward Jones, or American Family Insurance. Email subjects include:
- Complete with DocuSign: Your Payment Remittance is Available for Signing
- Complete with DocuSign:Remittance Notification – Signature Requested
- Complete with DocuSign: Your Payment Remittance is Available for Signing
- Complete with DocuSign: Payment Remittance – Please Review and Sign via DocuSign
- [Info]: Completed Document Ready for Your Review
- [Info]: Proposal Document Ready for Review
- [Sales]: Completed Document Ready for Your Review
- [Sales]: Proposal Document Ready for Review
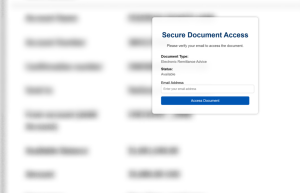
Upon clicking the provided link, a file opens to reveal a blurred document and an overlay requesting the user to verify their email address to view the document. Users will also be requested to enter Microsoft credentials into an official-looking login page. While it may appear to be a legitimate website, the credentials entered are forwarded to the threat actors by utilizing a synchronous relay, which is a form of an Adversary-in-the-Middle (AitM) attack that allows threat actors to intercept user input in real time.
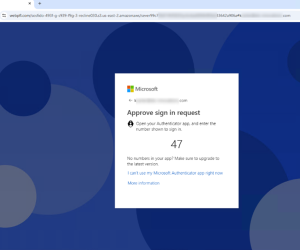
In the final stages of this campaign, the threat actor attempts to gain authenticator approval. If this sign-in request is approved through the legitimate application, threat actors can capture the session cookie, allowing them access and completely bypassing the need for MFA.
Recommendations
- Facilitate user awareness training to include these types of phishing-based techniques.
- Avoid clicking links and opening attachments in unsolicited emails.
- Confirm requests from senders via contact information obtained from verified and official sources.
- Review the Don’t Take the Bait! Phishing and Other Social Engineering Attacks NJCCIC product for more information on common phishing and social engineering attacks.
- Ensure MFA is enabled for all online accounts.
- Immediately change passwords and revoke active session tokens if entered into malicious websites.
- Report phishing and other malicious cyber activity to the NJCCIC and the FBI’s IC3.