’Tis the Season for Infostealing
Malware
November 21, 2024
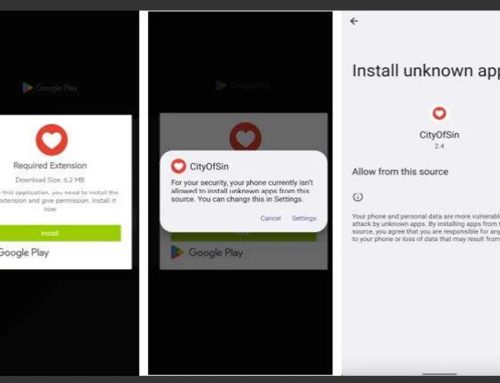
Threat actors actively seek methods to conceal their identities in information-stealing campaigns, aiming to lure individuals into downloading malicious software or revealing sensitive information. One recent campaign infects Windows devices with Lumma Stealer and infects macOS devices with AMOS infostealing malware. Both infostealers can steal cookies, credentials, cryptocurrency wallets, credit cards, and browser history from many popular browsers. In this campaign, the threat actors promote an AI video and image editor using X, promising 25 free uses a day. Upon clicking the ad, users are redirected to a professional-looking website that leads users to download a disguised version of either Lumma Stealer or AMOS.

A second campaign impersonates a popular and trusted password manager, Bitwarden. Threat actors are using Facebook to share advertisements, alerting users that their Bitwarden browser extension is outdated and warning them that their saved passwords are at risk. The advertisement directs users to a page imitating the official Chrome Web Store, utilizing chromewebstoredownload[.]com as the domain to avoid suspicion. Unlike the official web store, users are directed to download a ZIP file from a Google Drive link, enable Developer Mode through their browser’s extension settings, and manually load the unpacked extension. Once installed, the malicious extension collects Facebook cookies, user details, account information, and billing data.

A final infostealing campaign targets users searching for Black Friday sales. First spotted in October, this campaign imitates well-known brands, like L.L. Bean, Wayfair, The North Face, Bath & Body Works, and IKEA. These imitation websites are well crafted and offer steep discounts to lure potential victims into providing their credit card information. The domains for these impersonated sites often include “blackfriday,” and utilize the top-level domains (TLDs), “.shop,” “.vip,” “.store,” and “.top.” These websites use Stripe as the payment processor to add a sense of legitimacy, though it does not prevent the threat actors from stealing entered payment information. If payment information is entered into these malicious websites, threat actors can steal both the payment and card details.
Recommendations
- Avoid clicking on ads, social media links, and promoted search results.
- Users should only submit account credentials and payment information on official websites.
- Users are advised to only download applications from official sources.
- Users who downloaded the affected apps are urged to uninstall them promptly.
- Credentials used to log into malicious apps should immediately be changed.