TOAD Attacks Continue to Hop Along
Scams
July 3, 2025
The NJCCIC continues to observe Telephone-Oriented Attack Delivery (TOAD) attacks. Threat actors begin the attack by performing reconnaissance on their targets, gathering information from various sources such as past data breaches, data purchased on the dark web, and social media profiles. They leverage a combination of business impersonation, phishing emails, and fraudulent call centers. The TOAD emails employ callback phishing in which threat actors use legitimate phone numbers to impersonate customer service or assistance representatives. The emails typically contain a fake bill or receipt for a large payment, which creates an urgency to call the provided phone number. This tactic encourages targets to initiate the interaction, and it tricks them into divulging sensitive information or making fraudulent transactions, potentially resulting in credential theft, loss of funds, malware installation, and ransomware.
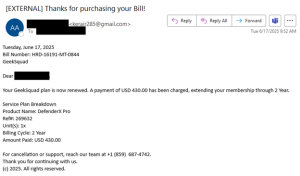
The NJCCIC’s email security solution detected several TOAD phishing campaigns sent to New Jersey State employees in the past month. In the above campaign, the email messages appear to be a GeekSquad subscription renewal and contain a phone number for cancellation or support. The threat actors create and use multiple Gmail email accounts, and the sender’s display name and the target’s name are the same. The subject line in the message starts with “Thanks for purchasing your” or “Payment completed for” and ends with “Bill,” “Invoice,” “Order,” “Receipt,” or “Transaction.”
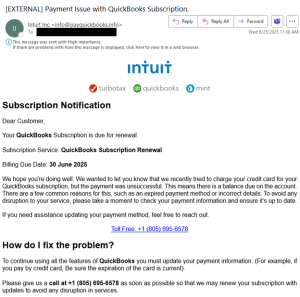
In a similar campaign, the email messages claim to be a notification for a QuickBooks subscription renewal and contain a phone number for assistance. The threat actors use “Intuit” in the sender’s display name but spoof “QuickBooks” or reference “renewalteam” in the sender’s email address, making the email message appear legitimate. They insert “Payment Issue with QuickBooks Subscription” or “Your Quickbooks Subscription Under Renewal” in the message’s subject line.
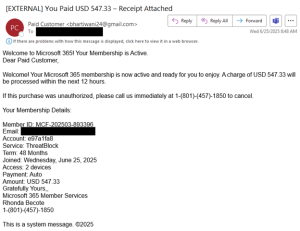
In another campaign, the email messages appear to be a Microsoft 365 subscription renewal and contain a phone number for assistance if the purchase was unauthorized. The threat actors create and use multiple Gmail email accounts with “Paid Customer” in the sender’s display name. The subject line in the message references “Receipt Attached,” “Microsoft 365,” “Payment Confirmation,” “Cancellation Confirmation,” “Subscription Invoice,” or “Payment Details.”
The NJCCIC also received reports of TOAD attacks targeting New Jersey residents and businesses. Several reports purported to be Norton subscriptions and Microsoft tech support services, resulting in some targets downloading a file and granting the threat actors remote access to their devices and financial accounts to steal personal information and funds. In another report, the target received a text message supposedly from the Apple Store about a declined transaction for $583.02. Once the target called the phone number in the text message, the threat actors claimed that the target’s identity had been compromised. They also advised the target to obtain a new Social Security number and move funds to a government-protected Bitcoin account, resulting in a loss of approximately $20,000.
Researchers also discovered PDF payloads containing specific phone numbers for callback phishing to confirm a transaction or resolve an issue. Most phone numbers in TOAD attacks are Voice over Internet Protocol (VoIP) numbers, which are harder to trace back to a specific individual or physical location than traditional phone numbers. These phone numbers can also be reused for consecutive days because they maintain a credible “brand” presence, minimize costs, and remain under the radar until discovered.
Recommendations
- Refrain from responding to unsolicited communications, clicking links, or opening attachments from unknown or untrusted senders.
- Exercise caution with communications from known senders.
- Confirm requests from senders via contact information obtained from verified and official sources.
- Type official website URLs into browsers manually and only submit account credentials and sensitive information on official websites. Legitimate customer support will never request account credentials or sensitive information over the phone.
- Use strong, unique passwords for all accounts and enable MFA where available, choosing authentication apps or hardware tokens over SMS text-based codes.
- If the account has been compromised, log out of all devices, revoke any access tokens, and reset passwords.
- Keep systems and browsers up to date.
- Reduce your digital footprint so threat actors cannot easily target you.
- Employ tools such as haveibeenpwned.com to determine if your personally identifiable information (PII) has been exposed via a public data breach.
- Review the Identity Theft and Compromised PII NJCCIC Informational Report if your PII has been compromised.
- Report malicious cyber activity to the NJCCIC and the FBI’s IC3.





