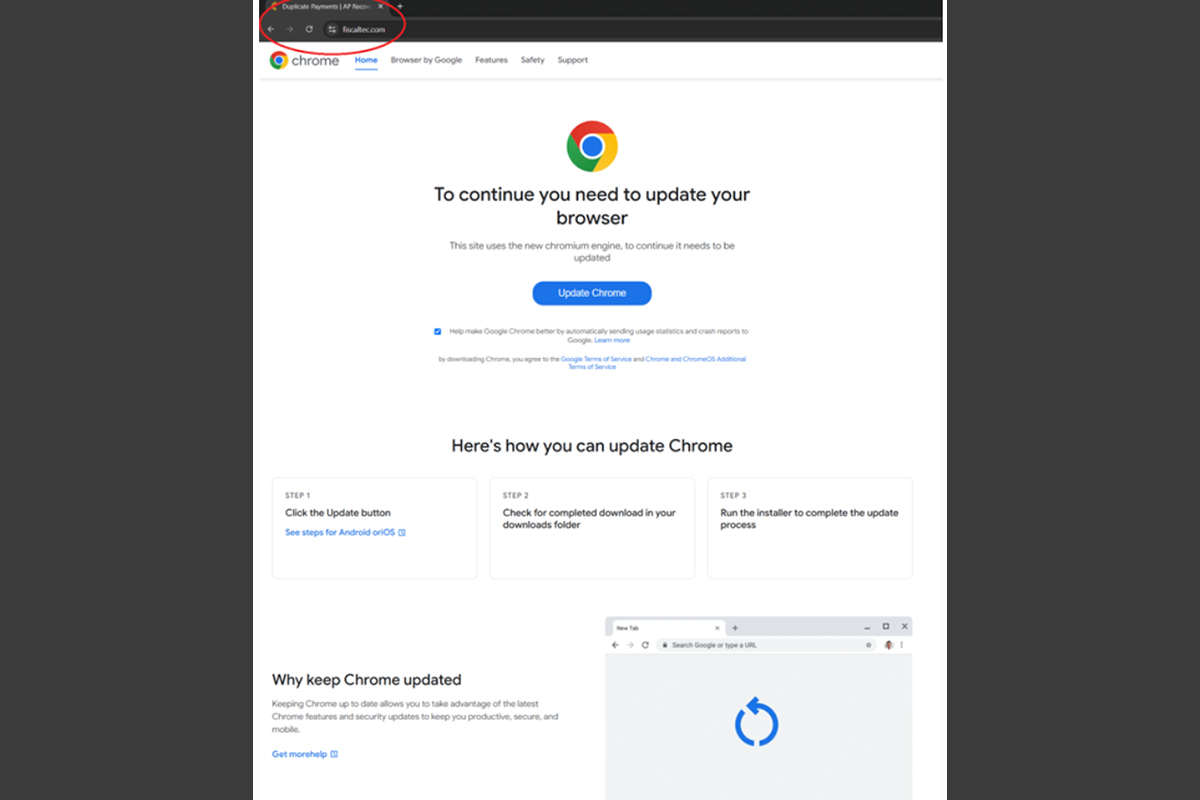
Update Your Browser to Continue
Scams
June 19, 2025
The NJCCIC’s email security solution has observed an increase in fake web browser update phishing campaigns. These campaigns begin with an email containing a link to a compromised website. The compromised website has a JavaScript inject that checks for the following conditions:
- Checks to see if the visitor is using Chrome on Windows.
- Checks the local storage to ensure the current browser won’t display the iframe after three visits.
- Checks that the “Update Chrome” button on the fake update page hasn’t been clicked within the last 30 days.
In one instance, after the checks are passed, an iframe overlay loads over the page, stating that a Chrome browser update is required to load the webpage. Clicking the “Update Chrome” button will lead to the download of Vidar and DeerStealer malware.
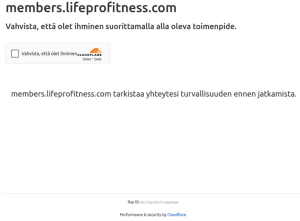
A second chain has also been spotted utilizing ClickFix tactics. After the above checks have passed, an iframe overlay loads, displaying a fake localized CAPTCHA that instructs a user to copy and execute a PowerShell script using the Windows command line. After executing the script, a malicious PowerShell payload will run and download Rhadamanthys.
Recommendations
- Facilitate user awareness training to include these types of phishing-based techniques.
- Avoid clicking links and opening attachments in unsolicited emails.
- Confirm requests from senders via contact information obtained from verified and official sources.
- Review the Don’t Take the Bait! Phishing and Other Social Engineering Attacks NJCCIC product for more information on common phishing and social engineering attacks.
- Maintain robust and up-to-date endpoint detection tools on every endpoint.
- Consider leveraging behavior-based detection tools rather than signature-based tools.
- Report phishing and other malicious cyber activity to the FBI’s IC3 and the NJCCIC.