Uptick in Business Email Scams
Mitigation,Scams
April 11, 2024
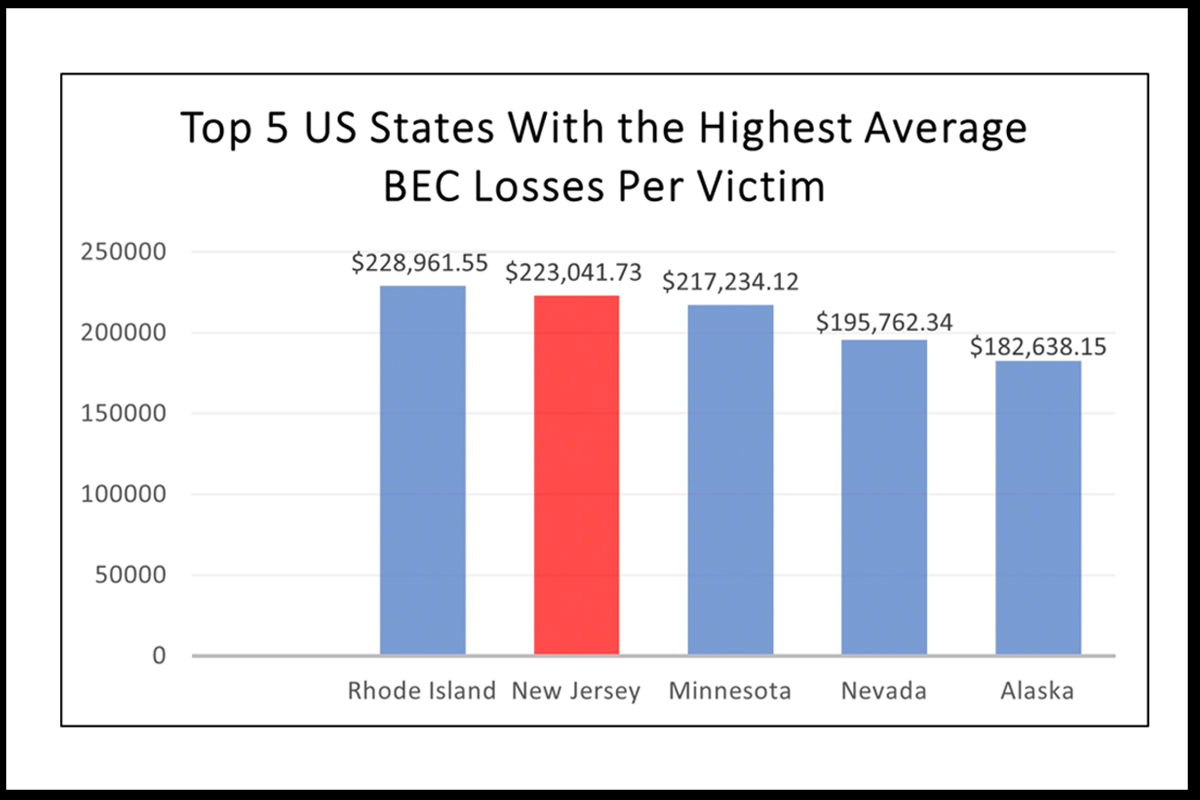
According to the FBI IC3 Internet Crime Report 2023, business email compromise (BEC) scams are the second most expensive type of cybercrime. Over the past three years, the number of US victims increased from 19,954 (2021) to 21,832 (2022) but decreased slightly to 21,489 (2023). However, the reported losses from BEC scams showed an upward trend of $2.3 billion (2021) to $2.7 billion (2022) to $2.9 million (2023). Additionally, New Jersey claimed 628 victims in BEC scams in 2023 and ranked second in the nation with an average loss per victim of $223,041.73. There was a significant increase in the total reported losses from 2022 (almost $63 million) to 2023 (over $140 million), and the trend is likely to increase.
Unlike generic phishing scams, BEC scams are a highly targeted form of social engineering, often incorporating preliminary reconnaissance on potential victims and using various impersonation techniques, including email spoofing and look-alike domains. To convey a sense of legitimacy, threat actors commonly spoof a familiar contact’s source name or email address, use domain names that mimic a trusted source, or compromise a legitimate account. The messages typically instruct the target to transfer funds or other sensitive information to the threat actors posing as trusted individuals. Common types of BEC attacks include wire transfer scams, direct deposit scams, real estate wire transfer scams, W-2 scams, and invoice scams. BEC scams can result in system compromises, data breaches, financial losses, and reputational damages.
The NJCCIC observed an uptick in various BEC scams, especially invoice, direct deposit, and real estate wire transfer scams. In invoice scams, threat actors impersonate trusted vendors with whom the target organization does business. They send emails to redirect outstanding and future invoices for products or services to a new bank account. Threat actors may attach legitimate or fraudulent invoices with inflated amounts and provide new payment policies with payment instructions and updated bank account details to steal funds from the vendor’s customers.
In direct deposit or payroll diversion scams, threat actors impersonate an employee, typically by registering a free email address using the employee’s name and utilizing display name spoofing in the messages. They usually send fraudulent emails to payroll or human resources departments, and direct deposit change forms are requested. Sometimes, the threat actors locate an organization’s direct deposit change form online and include a filled- out form in the email. They intend to divert an employee’s direct deposit account information to an account under the threat actor’s control. These emails may have noticeable red flags; however, they may be well-crafted and more challenging to identify as suspicious.
In real estate wire transfer scams, threat actors impersonate and target real estate attorneys or title agents to defraud homebuyers. These requests typically instruct the buyer to perform a wire transfer and transfer the closing costs to an account controlled by the threat actors. The attorney’s signature in the spoofed email may contain information obtained from the law firm’s website or social media platform. The subject and body of these emails often portray a sense of urgency to entice targets to provide sensitive information or immediately wire money before they can thoroughly review the email’s content and question its legitimacy. If successful, funds are transferred to the threat actors before the fraud scheme is detected.
The NJCCIC recommends that users and organizations educate themselves and others on these continuing threats and tactics to reduce victimization. Users are advised to refrain from responding to messages, opening attachments, and clicking
links from unknown senders and exercise caution with emails from known senders. If correspondence contains changes to payment options or bank information or is otherwise suspicious, contact the sender via a separate means of communication—by phone using contact info obtained from official sources or in person—before providing sensitive information or funds. Navigate directly to legitimate websites and verify websites prior to submitting account credentials or providing personal/financial information. We advise users to implement security controls that help prevent account compromise, including establishing strong passwords and enabling multi-factor authentication (MFA) where available, choosing authentication apps or hardware tokens over SMS text-based codes.
Organizations are advised to implement filters at the email gateway to identify and block emails using known phishing tactics and those from suspicious IPs, create an email gateway rule to flag communications in which the “reply” email address is different from the “from” email address, and identify emails that come from external sources outside their network by marking them with an “external email” tag in the subject and body since these emails should be given additional scrutiny. Furthermore, create a policy and procedure to identify and report BEC emails, including periodic employee awareness training; establish policies and procedures that require any requests for highly sensitive information or large financial transactions be authorized and approved by multiple individuals via a secondary means of communication beyond email; and implement Domain-Based Message Authentication, Reporting, and Conformance (DMARC) to reduce the risk of email spoofing. Organizations are also advised to implement procedures to prevent unauthorized direct deposit changes, such as requiring two levels of approval and verbal agreement from the requesting employee. Those who receive suspicious communications from a supposed known contact are encouraged to call the employee to verify any requests. Furthermore, all users are encouraged to maintain awareness of common red flags in malicious email messages, such as display name spoofing tactics.
Also, those involved in real estate transactions are advised to educate themselves and others and remain vigilant during and immediately after closing. Real estate businesses, including real estate attorneys and title agencies, are advised to implement new policies to prevent fraudulent wire transfers and other scams. For example, forbid the sharing of wire transfer account information via email and instead utilize video chat applications, phone calls from trusted numbers, or in-person meetings. Additionally, buyers should never trust email as the sole source of instruction for wiring money related to these transactions; instead, they should receive confirmation of these details in person or over the phone. Furthermore, digital escrow services can safeguard the interests of real estate buyers and sellers.
If funds are unintentionally wired to a fraudulent account, immediately notify a supervisor, banking institution, the FBI, and the US Secret Service so that attempts can be made to stop the wire transfer. Unless the fraudulent transaction is discovered quickly (typically within 48 hours), it can be difficult, if not impossible, to return the stolen funds. These types of scams should be reported to the associated entity or individual immediately, as well as the FTC, FBI’s IC3, and the NJCCIC to limit proliferation. Additional recommendations can be found in the Don’t Be Fooled: Ways to Prevent BEC Victimization NJCCIC Informational Report. If personally identifiable information (PII) has been compromised, review the Identity Theft and Compromised PII NJCCIC product for additional recommendations and resources, including credit freezes and enabling MFA on accounts.