Uptick in Card Skimming Scams
Scams
June 20, 2024
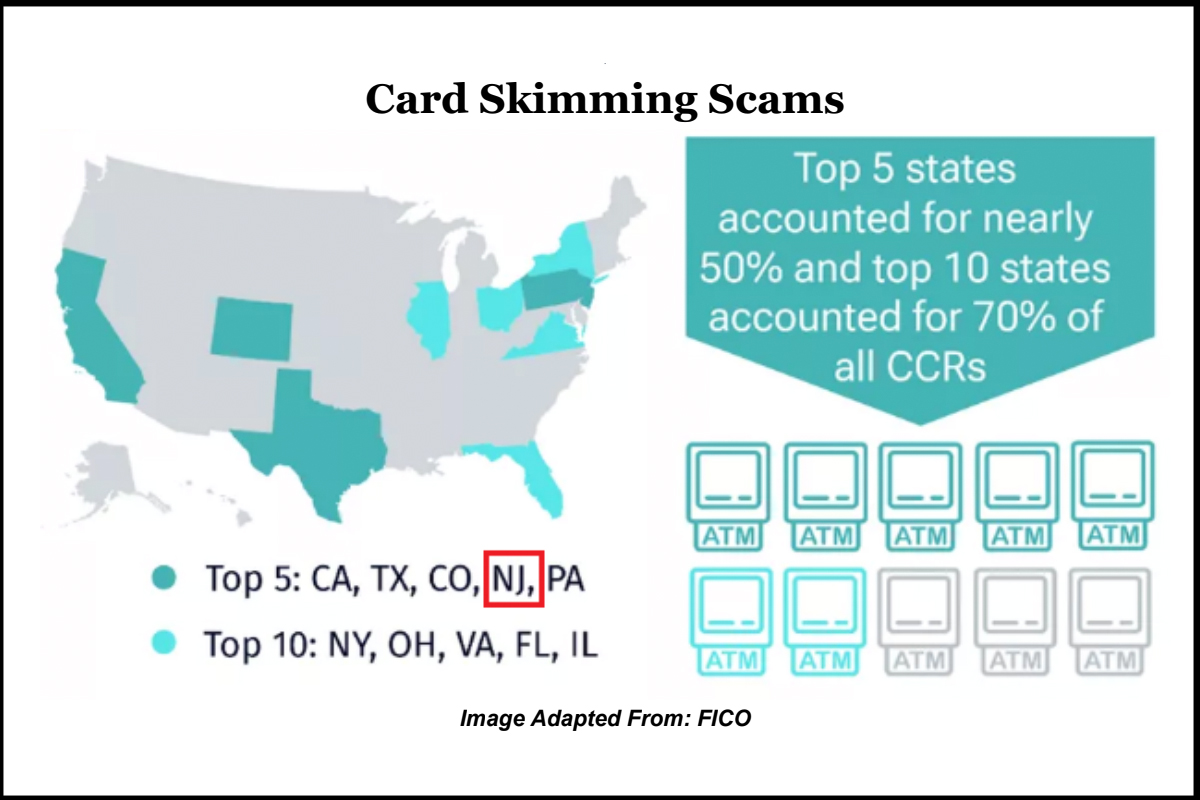
Reported card skimming incidents increased by 40 percent from 2022 to 2023. More specifically, New Jersey is one of the top five states, accounting for nearly 50 percent of card compromise reports (CCRs). The outlook for 2024 shows a continued upward trend, which means increased card skimming opportunities for threat actors to capture and steal customer data and financial information through various physical and digital methods. Threat actors seek methods to conceal their attacks better and evade multiple security measures. This stolen data has severe consequences for consumers and businesses, including loss in revenue, legal damages, compliance issues, cross-site contamination, compromised personally identifiable information (PII), identity theft, fraud, and subsequent malicious activity.
Physical skimming devices are typically located at ATMs and point of sale (POS) systems, such as convenience stores, grocery stores, retail stores, gas stations, and restaurants. In addition to skimmers, hidden cameras and fake numerical keypads can capture and record keystrokes of PINS or passwords. Once the card is swiped, the skimming device stores the victim’s information, which can be physically retrieved later by the threat actors. However, the increasing use of cellular and Bluetooth technologies enables threat actors to remotely access data quickly with a low likelihood of detection.
Since the onset of 2024, physical skimmers have been identified and reported to law enforcement in New Jersey, including ATMs at Capital One Bank and Proponent Bank in Nutley, two ATMs at Wawa in Galloway Township, card readers at Dollar Tree and Walmart in Bayonne, and card readers at 7-Eleven stores in Cinnaminson and Pennsauken. Additionally, a skimmer was detected at Supremo Food Market in Pennsauken, and skimming devices were recently identified at Aldi Stores in Roselle and Union.
Furthermore, law enforcement charged a Lakehurst gas station employee with stealing customers’ information and making fraudulent purchases. Two men were also arrested for placing skimming devices on several Westfield ATMs to steal debit card information and use counterfeit debit cards in fraudulent cash withdrawals.
The online equivalent of physical skimming is digital or web skimming, found in POS systems such as retail stores, restaurants, financial institutions, and any online business that uses a POS provider. Magecart attacks are a type of web-based data skimming operation used to capture customer payment card data from the checkout pages of online stores. These attacks are accomplished by gaining access to the targeted website (either directly or through a supply chain attack), injecting malicious code into the checkout page to skim the desired data, and sending the information back to a threat actor-controlled server. Once threat actors steal the payment card information, they can use it to make fraudulent purchases or sell on the dark web or other marketplaces.
In February, researchers discovered threat actors exploiting a critical vulnerability, CVE-2024-20720, without user interaction. Threat actors inserted malicious XML code in the “layout_update” database table on Magento servers to create a persistent backdoor to the CMS controller and automatically inject malware and additional malicious payloads, including a fake Stripe payment skimmer designed to steal information from unsuspecting online shoppers.
In April, researchers found a card skimmer embedded in a fake Facebook Pixel tracker script, typically used to track advertisement-driven visitor activity on websites. Threat actors injected malware into compromised websites through tools that allow custom code, which monitors the fraudulent overlay and captures the card information if victims encounter a checkout page.
In May, threat actors exploited a vulnerability in WordPress in the Dessky Snippets plugin used by many websites. They added malicious PHP injections in the custom code on compromised websites. They altered the WooCommerce checkout process by manipulating the billing form and adding new fields to steal financial information. To add a sense of legitimacy, the threat actors used a tactic to reduce suspicion by turning off the autocomplete feature on the billing form to prevent web browsers from suggesting previously entered sensitive information and making it appear that the fields are standard inputs to complete the transaction.
Recommendations for Consumers
- When possible, use credit cards over debit cards for purchases, as credit cards often have greater consumer protections that limit a victim’s liability if fraudulent purchases are made.
- Enable payment charge notifications for every transaction on an account to be alerted of a fraudulent transaction as soon as it occurs.
- Before you use a POS system or ATM, check to see if there are signs of tampering.
- Use tap to pay or pay with your phone, as contactless or chip payment options are safer than swiping the card’s magnetic strip.
- Navigate directly to known, secure, and encrypted websites and designate or monitor one credit card for purchases, if possible.
- Enable multi-factor authentication (MFA) on every account that offers it, including any online shopping websites.
- Update browsers and use ad blockers.
Recommendations for Website Administrators
- Ensure hardware and software are up to date.
- Use strong, unique passwords for all accounts (admin, SFTP, database) and enable multi-factor authentication (MFA) on all administrative accounts at a minimum.
- Use only vetted first-party code.
- Use a web application firewall (WAF) to block and alert for potential code injection attacks.
- Block unauthorized transmission of personal data by implementing a Content Security Policy (CSP).
- Schedule routine website scans to identify changes in code composition.
Resources