Uptick in Latest Wave of Sextortion Scam
Scams
April 3, 2025
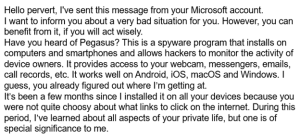
The NJCCIC has reported various classic sextortion scams in the past. Threat actors continue to utilize similar messaging but different domains, IP addresses, and cryptocurrency wallet addresses in their schemes. The NJCCIC received reports of the latest ongoing fraudulent scheme in which the threat actors’ tactics changed around mid-February and increased significantly in March. They claim they sent the message from the target’s compromised Microsoft account. Upon further inspection, they spoofed the target’s Microsoft email address such as Live, Hotmail, or Outlook. They use scare tactics and falsely claim to have installed the Pegasus spyware program on the target’s device and secretly recorded webcam footage of the target engaging in intimate activities. The threat actors then threaten the target with the release of compromising or sexually explicit photos or videos to family, friends, and coworkers in their contacts or social media platforms if a Litecoin (LTC) payment is not made within 48 hours, ranging from $1,250 to $1,800. The threat actors also claim they will receive a notification when the email is read, starting the 48-hour countdown. They also warn the target against replying to the email, contacting the police, and resetting or destroying the devices.
Recommendations
- Avoid clicking links, opening attachments, responding to, or acting on unsolicited communications.
- Refrain from sending funds and disregard these emails, as there is no indication that these threats are credible.
- Search for and report malicious cryptocurrency addresses in the scam email to Chainabuse.
- Report these scams to the FTC, the FBI’s IC3, and the NJCCIC.
- Reduce your digital footprint to reduce the likelihood of becoming a target for malicious actors.