Using DocuSign APIs to Bypass Security
Scams
November 7, 2024
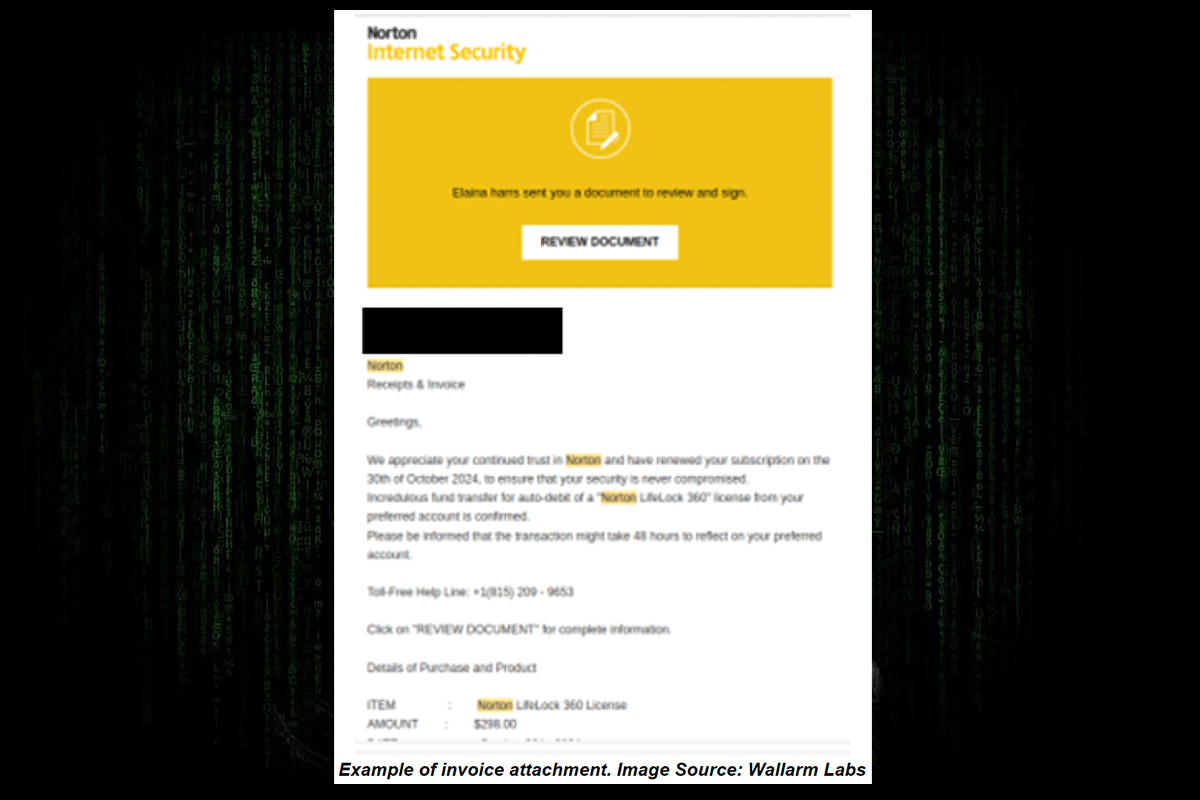
Consistent with open-source reporting, the NJCCIC’s email security solution detected increased attempts to exploit DocuSign APIs to deliver fraudulent invoices. Unlike traditional phishing scams, which rely on misleading emails and links, these attacks use real DocuSign accounts and templates to mimic reputable companies, making detection more difficult.
The threat actor creates a legitimate DocuSign account to manipulate templates and use the company’s API. They craft templates that mimic e-sign requests from recognizable brands like Norton Antivirus. These invoices may include real product pricing and additional fees, such as a $50 activation charge. If users e-sign, the threat actor may demand payment directly from the organization or forward the signed document to the finance department. Other observed attempts involve invoices designed to authorize payments sent directly to the threat actor’s bank account. Because these invoices are sent through DocuSign, they can bypass spam filters, appear authentic, and do not require the use of malicious links or attachments.
- Avoid clicking links, responding to, or otherwise acting on unsolicited emails.
- Confirm requests from senders via contact information obtained from verified and official sources.
- Keep systems up to date and apply patches after appropriate testing.
- Implement cybersecurity best practices to reduce risk and increase resiliency to cyber threats.
- Utilize monitoring and detection solutions to identify suspicious login attempts and user behavior.
- Conduct continuous monitoring and threat hunting. Ingest techniques found in the Wallarm article into endpoint security solutions.
- Consider leveraging behavior-based detection tools rather than signature-based tools.
- Report phishing and other malicious cyber activity to the FBI’s IC3 and the NJCCIC.