Vendor Email: Phishing Emails
Scams
October 20, 2023
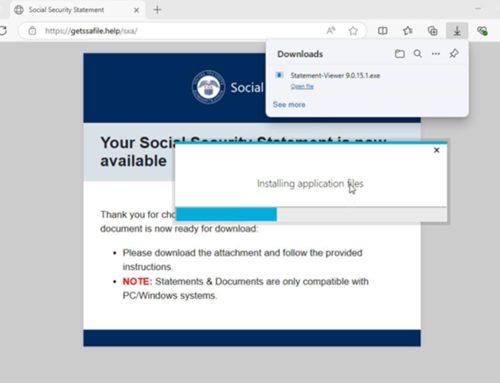
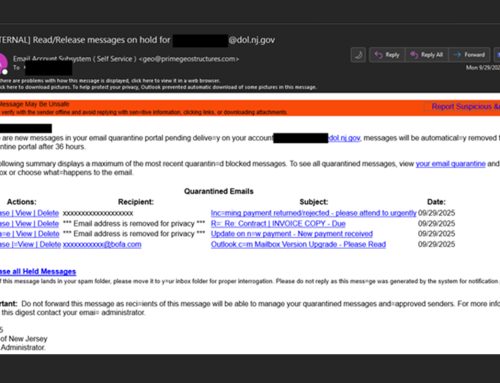
Vendor email compromise (VEC) is a targeted and in-depth type of business email compromise (BEC) in which cybercriminals impersonate a third-party vendor in order to steal funds from that vendor’s customers. Recently, Abnormal Security analysts detected a campaign in which a threat actor compromised various vendor email accounts belonging to individuals in accounting and operations roles and subsequently sent emails attempting to redirect outstanding and future invoices to a new bank account. These emails used similar messaging and contained a PDF attachment that outlined the fraudulent new payment policy, provided the updated bank account details, and in some instances, included fake invoices.
The NJCCIC continues to receive similar reports of impersonation scams in which threat actors pretend to be trusted vendors. The emails were sent from compromised vendor accounts; therefore, the sender’s email address and domain appeared normal to the recipients and bypassed scrutiny. Analysts determined that the targeted customer organizations were primarily critical infrastructure organizations, including those in the healthcare, logistics, and manufacturing industries.
What Should I Do?
The NJCCIC recommends users and organizations educate themselves and others on these continuing threats and tactics to reduce victimization. It is highly advised that users refrain from responding to unsolicited communications, clicking links, and opening attachments from unknown senders, and exercise caution with communications from known senders. If you are unsure of the legitimacy, contact the sender via a separate means of communication – such as by telephone– before taking any action. If correspondence contain changes to payment options or are otherwise suspicious, contact the vendor directly before providing sensitive information or funds. These types of scams should be reported to the associated vendor immediately, and the FTC, FBI’s IC3, and the NJCCIC to limit proliferation. Please contact us here at Cyber Command.