Voldemort Targets the Cyber World
Ransomware
September 5, 2024
Voldemort, a recently discovered backdoor, is spreading through a malware campaign that impersonates tax agencies. Beginning on August 5, the campaign sent over 20,000 messages to over 70 organizations worldwide. Initially, the daily malicious message count hovered in the low hundreds but saw a surge of activity on August 17, with nearly 6,000 messages sent.
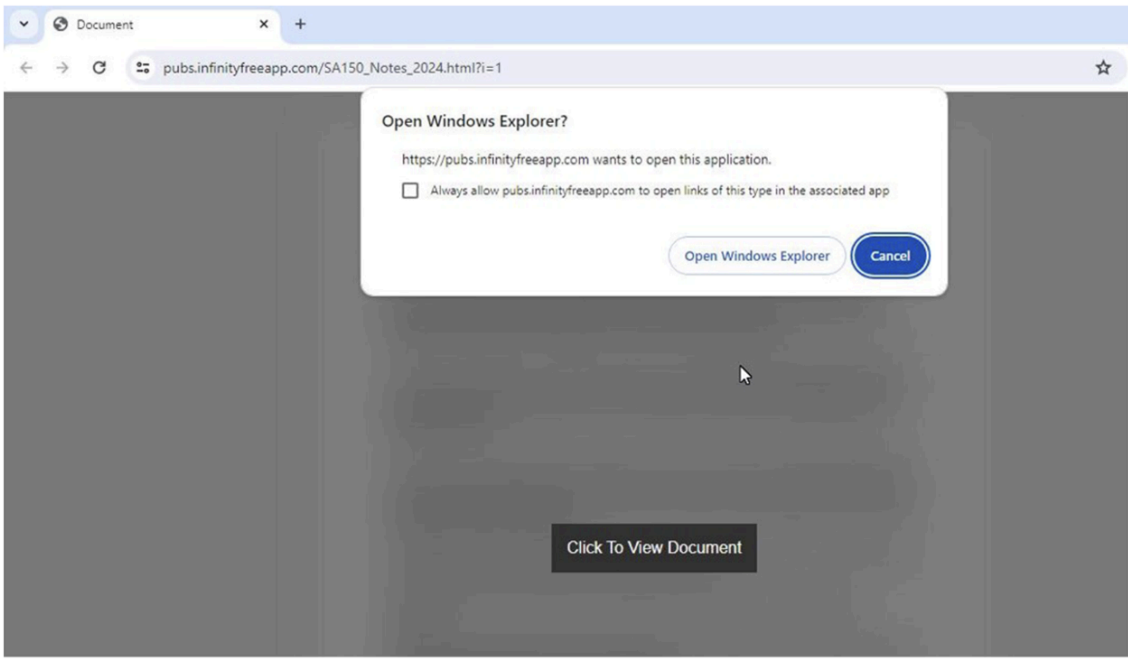
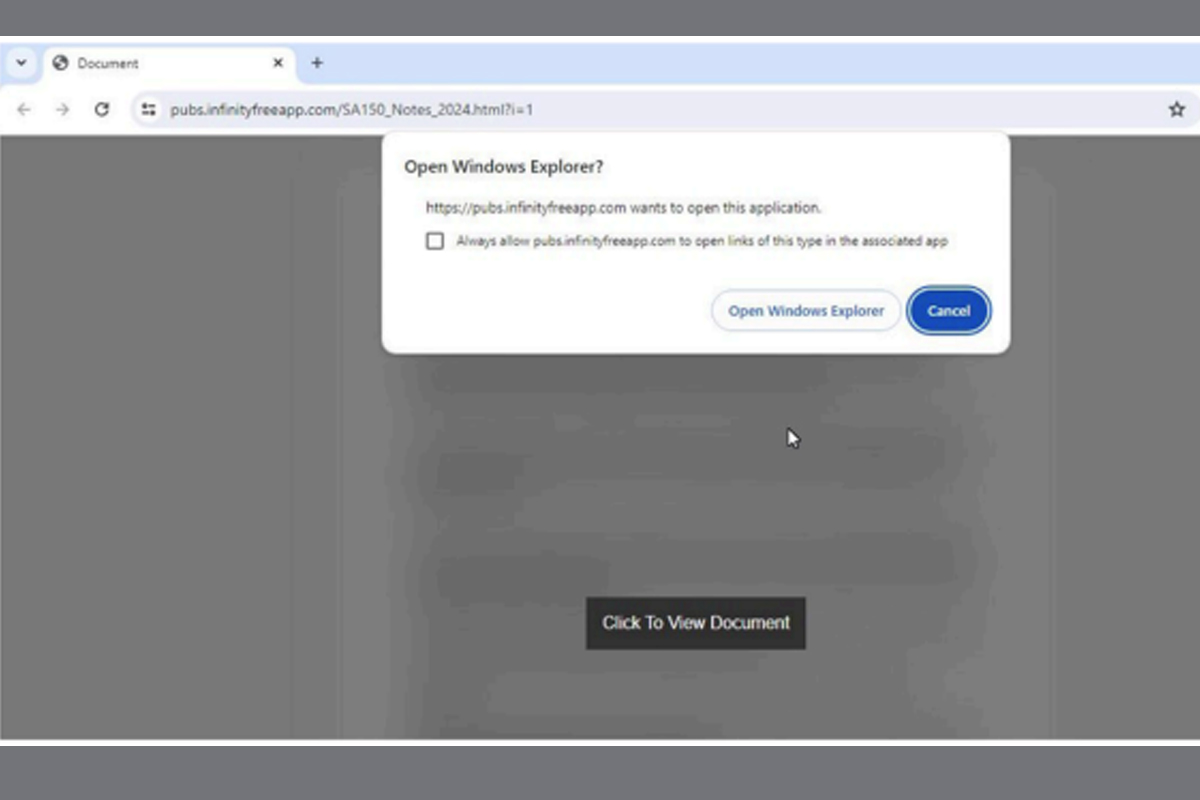
This campaign begins with a phishing email impersonating tax agencies localized to the targeted recipient. These emails include a link claiming to be documentation for important tax updates. Upon clicking the provided link, users will be redirected through Google AMP Cache URLs to a landing page hosted on InfinityFree. The landing page displays a “Click to View Document” link that checks the browser’s User Agent once clicked. If the malware finds the User Agent is Windows, the user will be sent to a search-ms URI (Windows Search Protocol) that points to a TryCloudflare-tunneled URI that prompts the user to open Windows Explorer. Non-Windows users will be sent to an empty Google Drive URL where the threat actors can track browser and network details without delivering malicious content.
If a user opens Windows Explorer, a Python script will be executed from a Web Distributed Authoring and Versioning (WebDAV) share to collect system information and profile the victim. The script also downloads a Cisco WebEx executable (CiscoCollabHost.exe) and a malicious DLL (CiscoSparkLauncher.dll) to side-load Voldemort. A PDF is displayed to hide the malicious activity. An unusual feature of Voldemort is its use of Google Sheets for its command and control (C2) server.
Emails delivered in this campaign impersonated tax agencies in the United States, the United Kingdom, France, Germany, Italy, India, and Japan. The threat actors targeted 18 different verticals, with insurance making up nearly a quarter of organizations hit. While Voldemort’s end goal remains unknown, security researchers suspect threat actors are aiming to conduct cyber espionage.
Recommendations
- Avoid clicking links and opening attachments in unsolicited emails.
- Confirm requests from senders via contact information obtained from verified and official sources.
- Type official website URLs into browsers manually.
- Facilitate user awareness training to include these types of phishing-based techniques.
- Maintain robust and up-to-date endpoint detection tools on every endpoint.
- Consider leveraging behavior-based detection tools rather than signature-based tools.
- Review the Don’t Take the Bait! Phishing and Other Social Engineering Attacks NJCCIC product for more information on common phishing and social engineering attacks.
- Report malicious cyber activity to the FBI’s IC3 and the NJCCIC.