Volt Reestablishes KV Botnet
Global Attacks
November 21, 2024
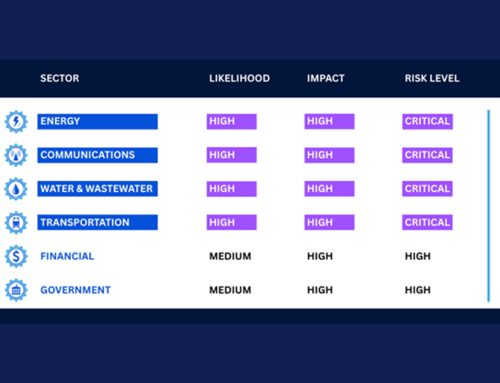
Analysts recently identified the resurgence of the KV botnet, an operational relay box (ORB) network associated with the Chinese APT group Volt Typhoon. Their modus operandi involves compromising outdated and end-of-life (EOL) SOHO networking devices like Cisco RV320/325 and Netgear ProSafe routers to rebuild the KV botnet. An ORB network is a proxy infrastructure composed of virtual private servers (VPS) or compromised devices that allow adversaries to relay communications and obfuscate detection while bypassing geofencing measures for defense evasion. The KV-Botnet may also be referred to as the ‘JDYFJ Botnet’ due to a unique self-signed SSL certificate named JDYFJ. Recent observations indicate a resurgence in scanning activity, which poses a significant threat to critical infrastructure.
Analysts also detected Volt Typhoon using a Microprocessor without Interlocked Pipelined Stages (MIPS)—based malware, similar to Mirai, and web shells that exploit the MIPS architecture to establish covert connections and communicate through port forwarding via 8433. MIPS-based malware specifically targets devices with 32-bit MIPS processors like routers and Internet of Things (IoT) devices. Webshells, such as fy.sh, are strategically implanted in routers, allowing the threat actor to maintain persistent access and remote control.
Researchers noted that Volt Typhoon compromised roughly 30 percent of all internet-exposed devices in just 37 days; however, how the devices were breached remains unknown. Additionally, Volt Typhoon was recently observed using a compromised VPN device located on the Pacific Island of New Caledonia as a bridge that functions as a discreet hub, routing traffic between Asia-Pacific and America.
Recommedations
- Implement cybersecurity best practices to reduce risk and increase resiliency to cyber threats.
- Avoid clicking links, responding to, or otherwise acting on unsolicited text messages or emails.
- Keep systems up to date and apply patches after appropriate testing.
- Use strong, unique passwords and enable multi-factor authentication (MFA) for all accounts where available, choosing authentication apps or hardware tokens over SMS text-based codes.
- Enforce the principle of least privilege, disable unused ports and services, and use web application firewalls (WAFs).
- Employ a comprehensive data backup plan and ensure operational technology (OT) environments are segmented from information technology (IT) environments.
- Perform scheduled backups regularly, keeping an updated copy offline in a separate and secure location and testing it regularly.
- Ingest IOCs into endpoint security solutions and consider leveraging behavior-based detection tools rather than signature-based tools.
- Report cyber incidents to the FBI’s IC3 and the NJCCIC.