Volt Typhoon Exploits Versa Vulnerability
Individual Attacks
August 29, 2024
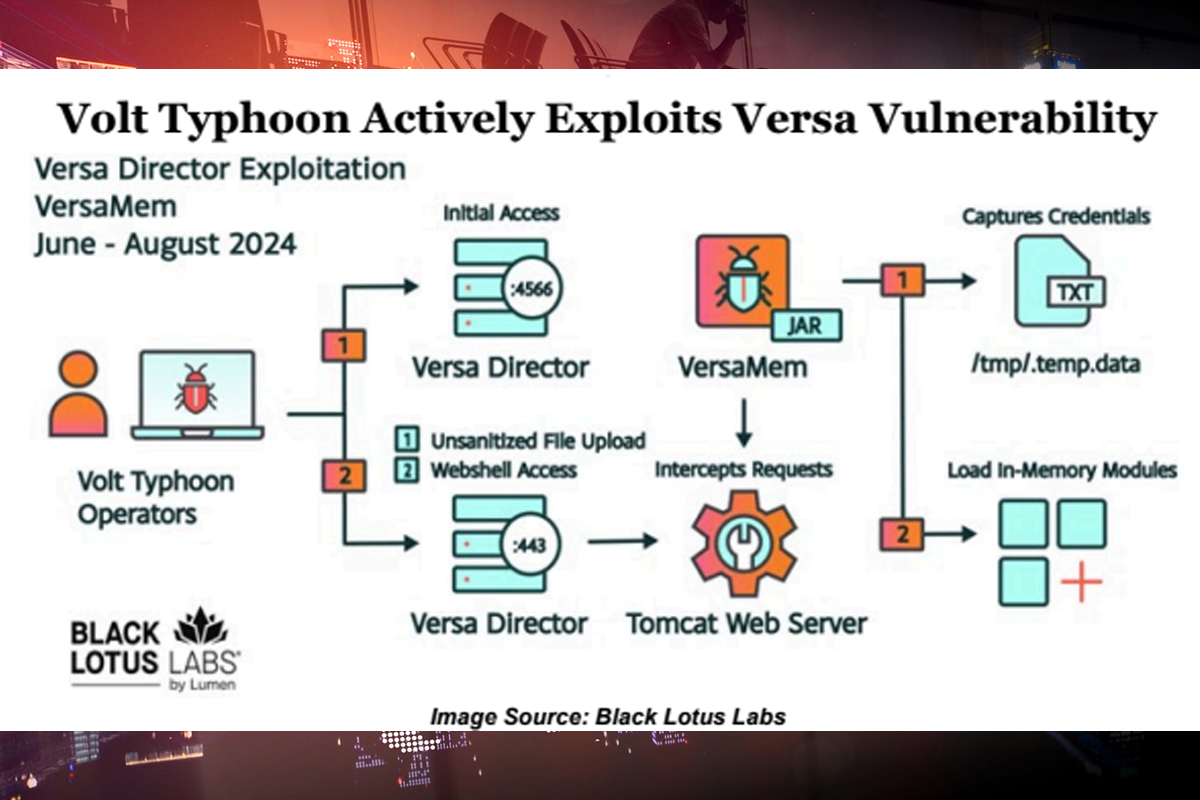
Analysts recently discovered at least one Advanced Persistent Threat (APT) actor actively exploiting CVE-2024-39717. The vulnerability impacts Versa’s Director GUI platform, which potentially allows malicious files to be uploaded by users with Provider-Data-Center-Admin or Provider-Data-Center-System-Admin privileges.
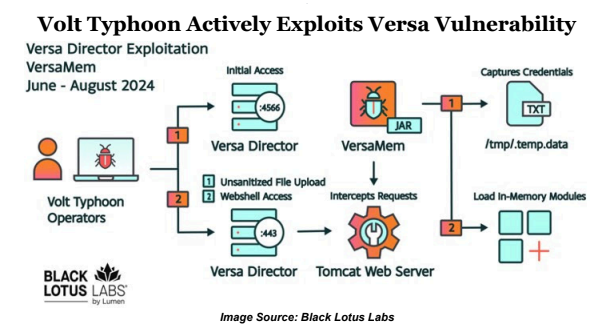
Black Lotus Labs identified a customized web shell, “VersaMem,” intended to intercept and gather credentials for network access. As early as June 12, 2024, at least five small- office/home-office (SOHO) devices victims were compromised, one being a non-US victim in the Internet service provider (ISP), managed service provider (MSP), and information technology (IT) sectors. Based on observed tactics, techniques, and procedures (TTPs), analysts determined that the zero-day exploitation of CVE-2024-39717 and the use of the VersaMem web shell can be attributed with moderate confidence to the Chinese state- sponsored threat actor, Volt Typhoon.
Versa provided the following recommendations:
- Apply Versa’s system hardening and firewall guidelines.
- Update Versa Director to a remediated version, which includes updates for versions 21.2.3, 22.1.2, and 22.1.3. Version 22.1.4 was not affected by the vulnerability.
- Inspect the /var/versa/vnms/web/custom_logo/ folder for any suspicious files having been uploaded. Running the command: file -b –mime-type <.png file> should report the file type as “image/png”.