.ZIP File Archiver Phishing Technique
Scams
June 1, 2024
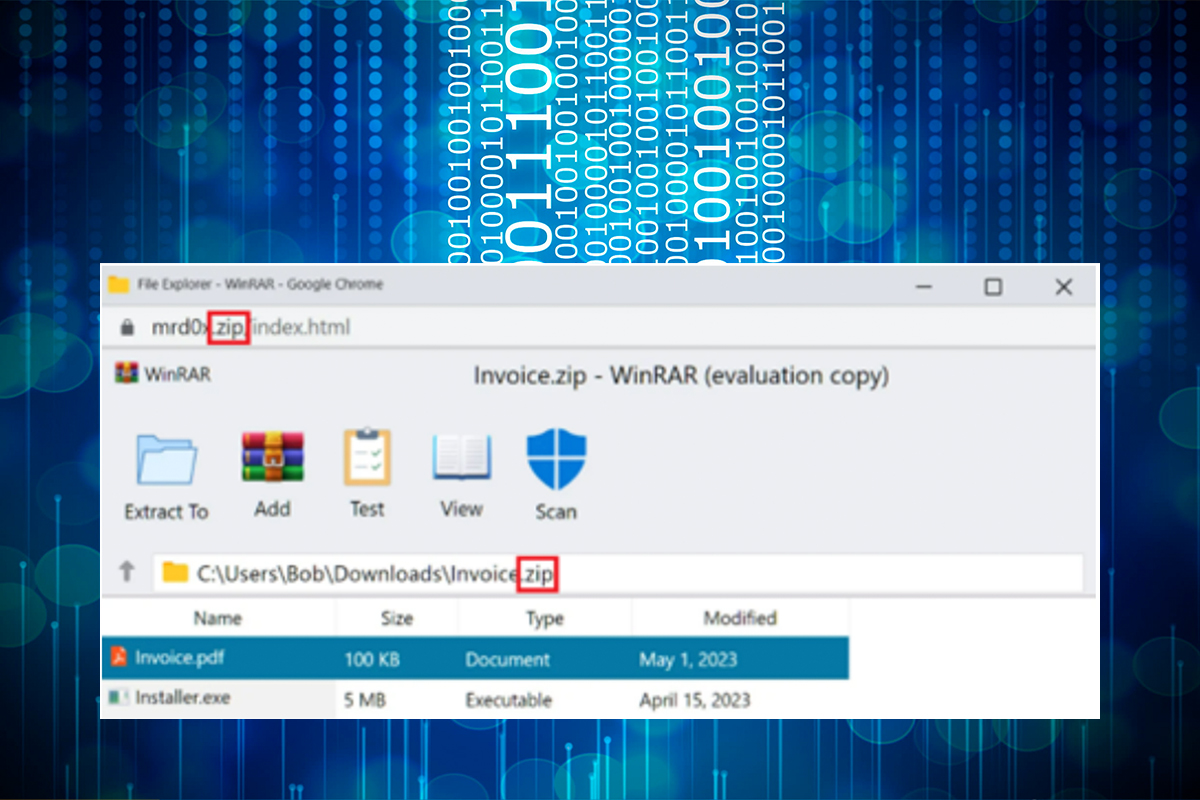
In May 2023, Google launched several new top-level domains (TLDs), including .ZIP. The use of .ZIP for filename extensions and domain names is legitimate; however, threat actors are exploiting the .ZIP domain name in a new phishing technique called “file archiver in the browser.” These .ZIP websites can automatically turn a string ending in .ZIP into a malicious link used in phishing campaigns to steal credentials or deliver malware. If clicked, the browser opens the .ZIP website, redirects the target to a website displayed as an HTML
page, and prompts the target to download the malicious .ZIP file. In the above example, when the .ZIP website is launched, a fraudulent WinRAR archiver software window is embedded in the browser to purportedly display an opened .ZIP archive and its contained files. To appear more convincing, a fraudulent security scan button is also displayed. If clicked, a message appears indicating that “the files were scanned and no threats were detected.” If one of these files is selected, the target is redirected to another website and prompted to enter their credentials to view the file.
The NJCCIC recommends users and organizations educate themselves and others on these continuing threats and tactics to reduce victimization. Users are advised to refrain from responding to unsolicited communications, clicking links or opening attachments from unknown senders, and exercise caution with communications from known senders. If unsure of the legitimacy, contact the sender via a separate means of communication, such as by phone, before taking action. Hover your mouse over the link to verify the URL before clicking or manually type the URL directly into your browser’s address bar. Once the website’s legitimacy is confirmed, bookmark the page when needed. Phishing emails and other malicious cyber activity can be reported to the FBI Internet Crime Complaint Center (IC3) and the NJCCIC.
For any further questions, contact us here at Cyber Command.