Cyber Command
Cyber Command Corporation is an IRS approved 501(c)(3) nonprofit, public charity that offers cybersecurity awareness training and develops viable cybersecurity defense software.
Mission Statement
Cybersecurity concerns are one of the most critical threats facing the security of our nation, which impacts all United States citizens, including individuals, families, businesses of all sizes and verticals, and government organizations.
Our mission is to reduce threat risk by promoting cybersecurity education and awareness, facilitating research, advancing development, and enabling dissemination of cybersecurity defense products and services to USA individuals, public and private organizations.
Want to organize a free virtual or in-person cybersecurity class for seniors in your neighborhood? Please contact us below and we’ll get the process started!
Cybersecurity Intelligence Feed & Resources
This section contains free cybersecurity related articles and knowledge to help learn critical cybersecurity lessons.
FinWise Bank Data Breach
FinWise Bank partners with American First Finance (AFF) to offer consumer financing products, including installment loans and lease-to-own programs. FinWise Bank, on behalf of AFF, disclosed a data breach involving a former employee who accessed sensitive data...
Threat Actors Hunting for Your Information
The NJCCIC has observed an increase in the distribution of infostealing malware. This type of malware is popular among threat actors because of the kind and amount of information it can exfiltrate. Infostealers often have capabilities that allow threat actors to retrieve credentials.
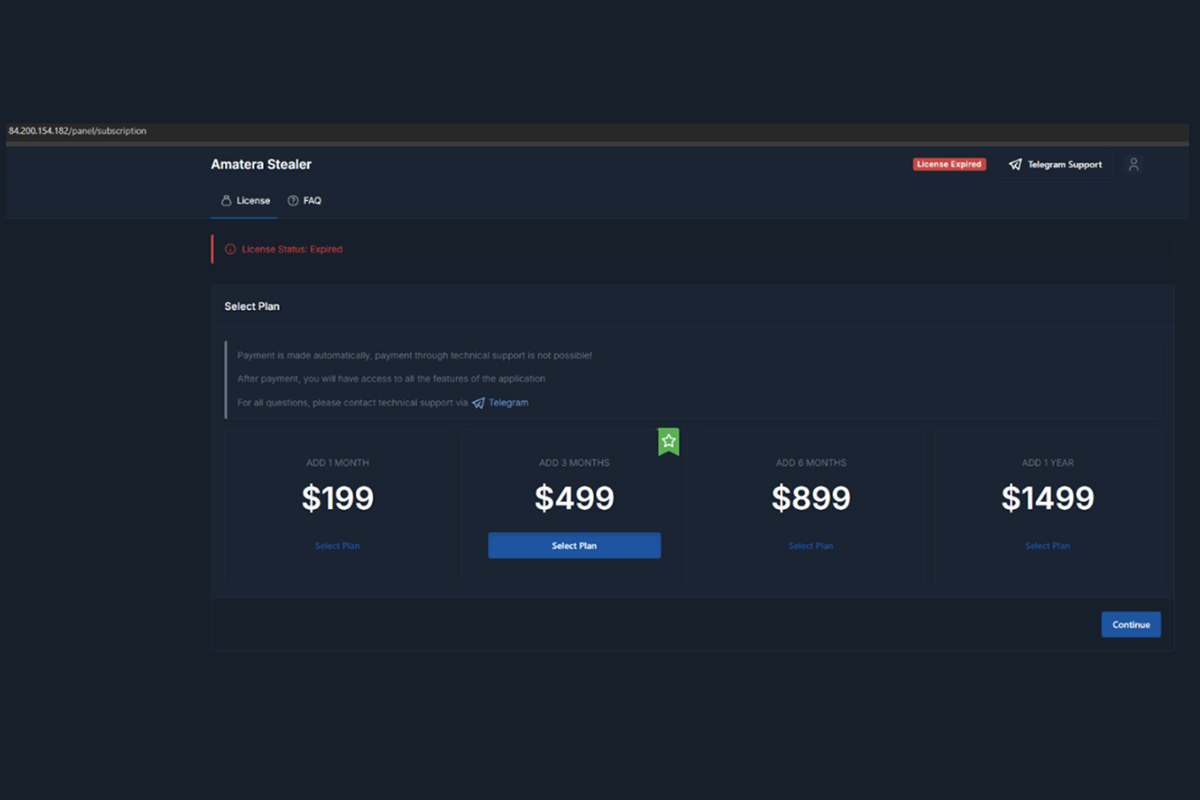
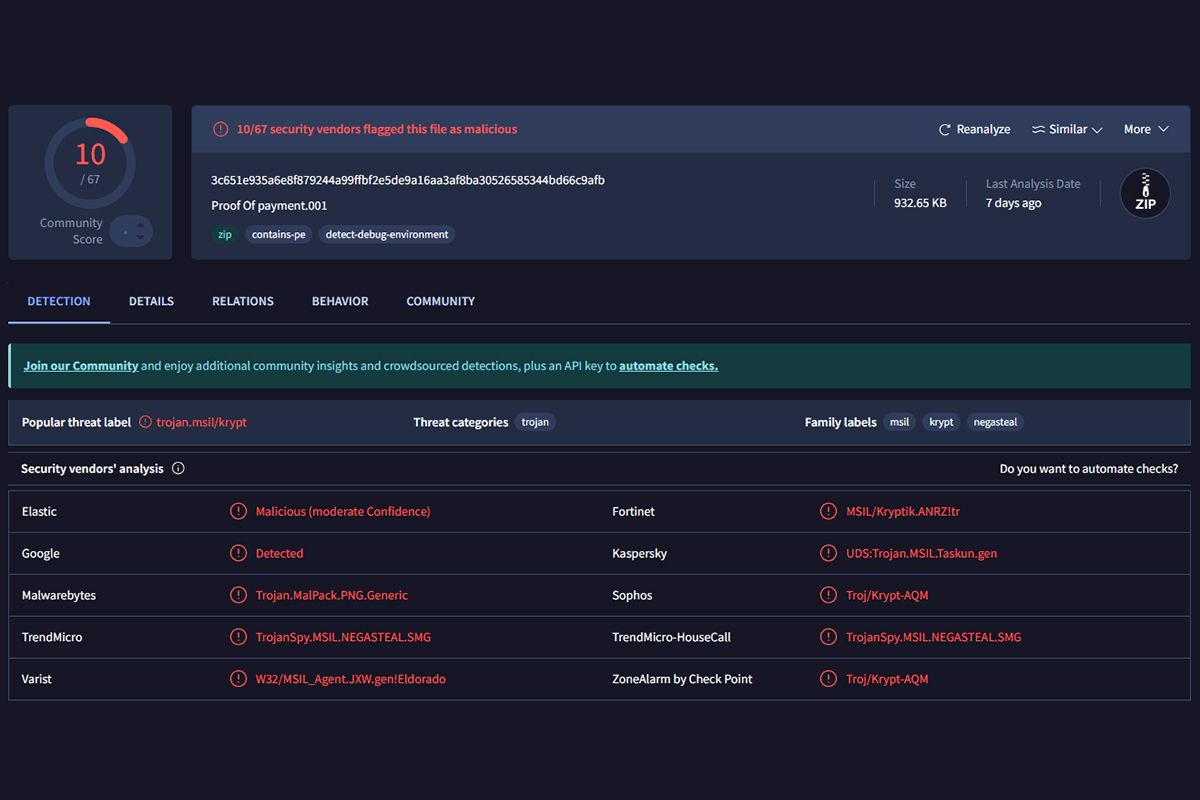
Beware of Malicious Proof of Payment
The NJCCIC observed a malware campaign sent to New Jersey State employees, purporting to be proof of payment. The malicious emails contain a ZIP file labeled “Proof Of payment.001” with a SHA-256 hash. The ZIP file appears legitimate but includes a Microsoft EXE file.
Multiple Vulnerabilities in Mozilla Products
Multiple vulnerabilities have been discovered in Mozilla products, the most severe of which could allow for arbitrary code execution. Successful exploitation of the most severe of these vulnerabilities could allow for arbitrary code execution. Depending on the privileges associated...
In Remembrance of September 11
As we commemorate the anniversary of the September 11, 2001 attacks, we pause to honor the victims, the courage and sacrifice of first responders, the resilience of survivors, and the families and communities impacted. This tragedy changed our nation and our state forever.
Threat Actors Steal More Than Romance
The NJCCIC continues to receive reports of romance scams targeting New Jersey residents to steal funds. Threat actors typically create fake accounts on social media platforms or dating apps to pose as potential new friends or love interests. They increasingly use AI as disguise...
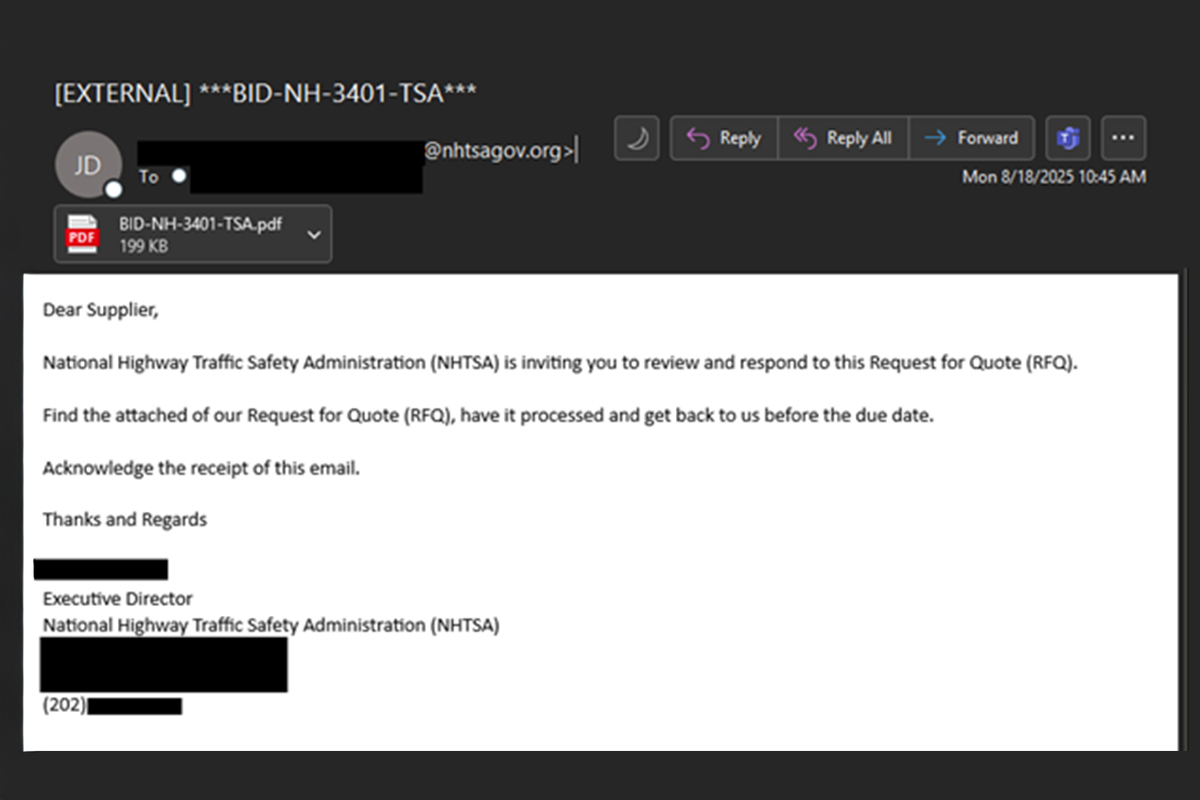
Look Both Ways Before Responding
The NJCCIC observed a phishing campaign imitating the US National Highway Traffic Safety Administration. In this campaign, threat actors send a phishing email containing a PDF file that looks legitimate and appears to be benign. To add credibility to the email, the threat actors use...
Fraudulent SMS Regarding Tax Refund
A new wave of SMS text phishing messages (SMiShing) is being sent to NJ residents and those in other states nationwide. Like previous SMiShing campaigns referencing motor vehicle violations and toll fees, these text messages impersonate the Division of Taxation and claim that a refund...
Critical Patches Issued for Microsoft Products
Multiple vulnerabilities have been discovered in Microsoft products, the most severe of which could allow for remote code execution. Successful exploitation of the most severe of these vulnerabilities could result in an attacker gaining the same privileges as the logged-on user.
Our Services
C3 helps reduce the risk of compromise by promoting cybersecurity education and awareness, and by facilitating research, development and dissemination of viable cybersecurity defense products and services to individuals, public and private organizations in the United States.
In-Person Training Classes
Virtual Classes
Phishing Simulations
Security Posture Analysis
Credential Leak Checks
Policies, Procedures & Plans
Phishing Attack Prevention
Network Intrusion Protection
Actionable Intelligence
Cyber Command is a registered 501(c)(3) nonprofit, public charity. EIN 93-2718000.
Our Board of Directors

Joshua Weiss, President

Arthur Warady, Treasurer

Kelly Whitis, Secretary
Contact Us
We’d love to hear from you. Please use the contact form below to reach us.